Detect and protect your data from a cloud account takeover by knowing these 5 indicators
Account takeovers are a growing concern for security and system admins in organizations of all types and sizes. A cloud account takeover impacts school districts that are using cloud applications, such as Google Workspace and Microsoft 365.
Cloud account takeovers are popular because hackers know how difficult it is for IT security teams to detect and defend against them. In the perimeter-less world of cloud computing, account takeovers are easier to accomplish and can have a much greater impact on a district’s information systems. Criminals can quickly gain access to more accounts and information than they could with software and on-premise servers protected by firewalls and MTAs.
What is a Cloud Account Takeover?
The basic mechanics and intent of a cloud account takeover is the same as an account takeover that occurs on-premise. A criminal gains access to an internal account, through any of a variety of means, and uses it to gain access to more accounts and more information they can use for their own purposes.
The ways that an account takeover can happen in the cloud can vary. The impact that it has in the cloud can also be a bit different. Perhaps the biggest differences are in a school district’s ability to detect a cloud account takeover, find out what the takeover impacted, and fix the issue.
Many K-12 districts that were quick to adopt cloud computing have been slow to adopt cloud computing security. There are 2 misconceptions contributing to this issue. First, admins think that their existing, network-based cybersecurity infrastructure is sufficient to protect cloud applications. Second, they tend to believe that the app providers are responsible for securing customer data.
Knowing what abnormal behavior looks like is an important first step in account takeover prevention. This knowledge helps you detect a cloud account takeover (or a takeover attempt), and then take the steps required to remediate it.
1. Login Location
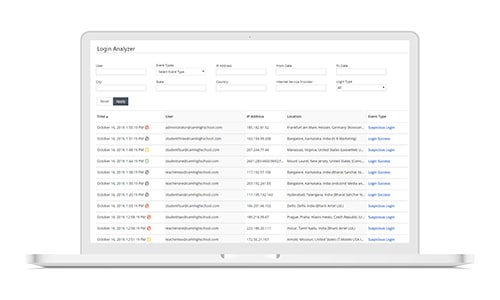
Using login location to detect a possible cloud account takeover is simple and works well for most districts. Analyzing login locations lets you see if there are login attempts originating outside of where you would normally expect to see them. Then, you can set cloud security policies against allowing logins and other activity from these locations.
For example, most school districts in the United States don’t have students or employees physically located outside of the country. If you suddenly see a spike in login attempts originating in China, you have a pretty good sense that this account is under attack.
Of course, people do go on vacation and foreign exchange programs, so that is something to consider. You may need to put policies in place that informs the IT staff when a specific users needs to access the school’s cloud environment from outside of the country. Best security practices tell us to err on the side of caution. Keep it locked down and let a legitimate user contact you to let you know if it needs to be unlocked.
2. Failed Login Attempts
According to a study by Signal Sciences, any given external application can expect to experience a login failure rate of about 30%. They happen. People forget their passwords, or enter them incorrectly, and sometimes the app server fails.
But many failed attempts over a short period of time is a good indication that a cloud account is under attack. A hacker may be using a bot to try out all the most common passwords, or different variations of a known password, to gain authorized access to the app.
A good idea is to set up policies that limit the number of failed login attempts before an account is locked out. Most will limit failed logins to 3 to 5. After that, the user needs to contact the app administrator to unlock the account and reset the password. You should also consider setting up an alert for the system admin in charge of applications and/or security, so they receive a notification when there have been multiple login attempt failures. This kind of visibility allows the admin to take proactive action to determine if the attempts are legitimate or malicious.
3. Lateral Phishing Emails
The first two are good ways to detect if someone is attempting an account takeover. The rest are how to detect a cloud account takeover that has already occurred. Monitoring your district’s applications for abnormal behavior is the best way to detect cloud account takeovers.
Lateral phishing emails originate from an account that has already been compromised. Because emails are sent from an internal account, lateral phishing is difficult to detect using traditional phishing filters. Lateral phishing attacks are relatively new and are gaining in popularity because they get around most traditional phishing filters and can impact many accounts.
A recent study found that 1 in 7 organizations experienced at least one lateral phishing attack in a span of 7 months. In total, researchers found 154 hijacked accounts that sent lateral phishing emails to over 100,000 unique recipients. The report goes on to identify that about 40% of the recipients were fellow employees, while the remaining were a variety of account types including personal, customer, partner, and vendor recipients.
Traditional mail transfer agents (MTAs) and phishing filters operate at the perimeter of your school district’s network. But what happens when a user isn’t in the network? Or if an account takeover has already occurred? These security tools don’t have the capability to detect further phishing attacks from within. If you are using a cloud security solution that scans emails and files for phishing links and malware inside email and shared drive accounts, your ability to detect such emails is much higher.
4. Malicious OAuth Connections
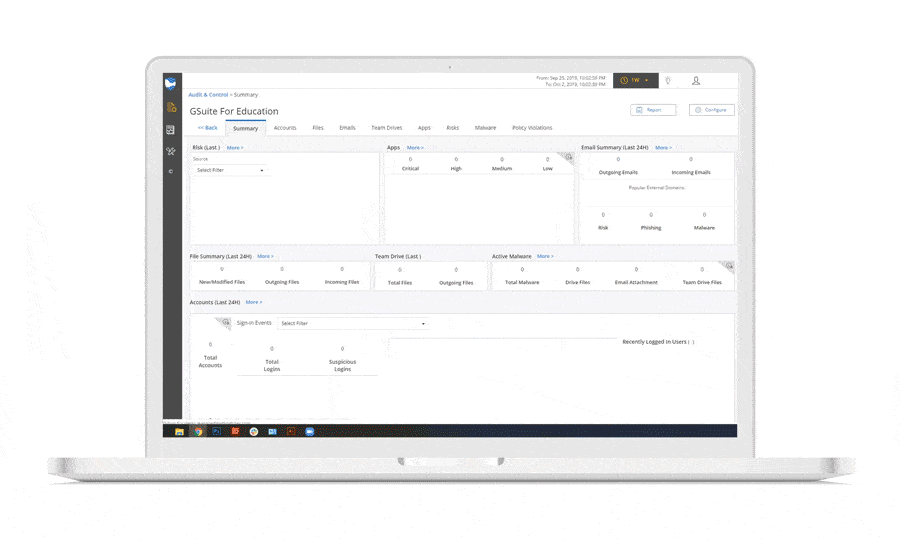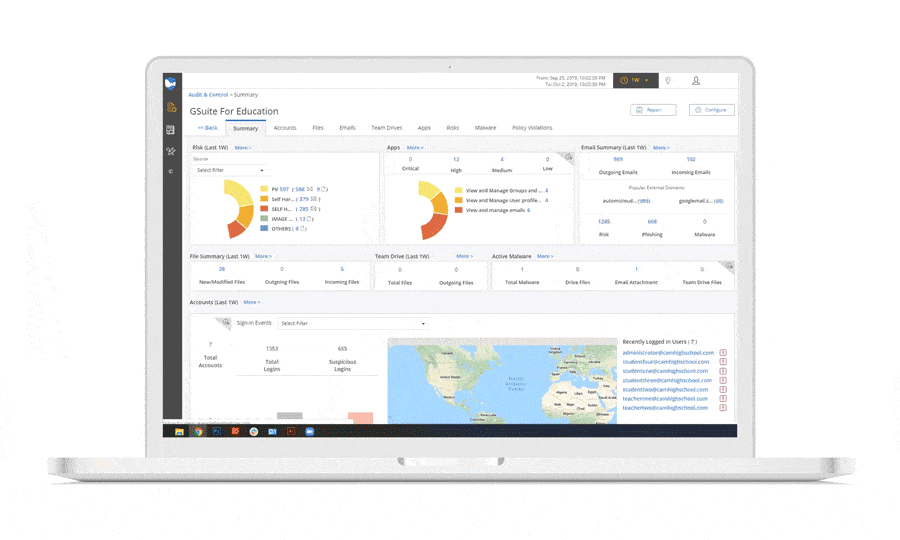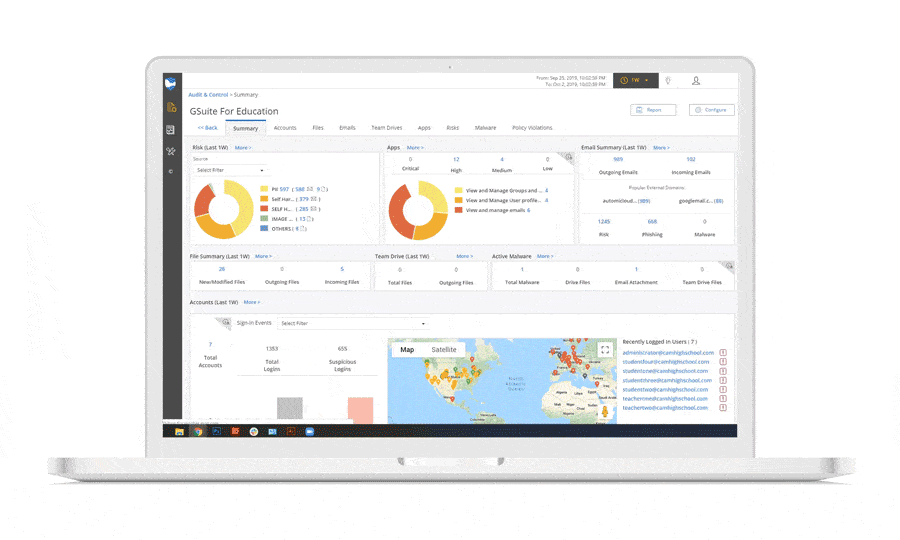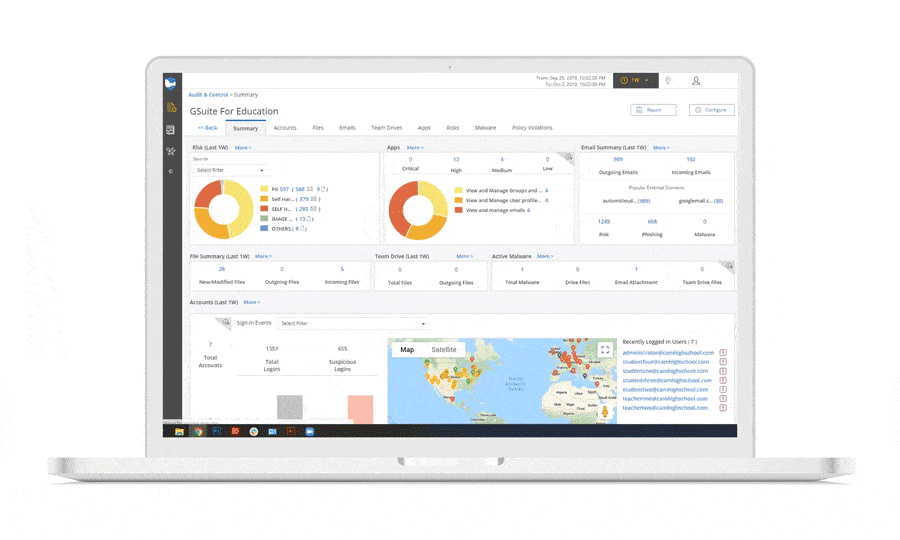
Connecting SaaS applications to the cloud environment through OAuth is now a common occurrence. Connecting to malicious apps is a behavior that can occur accidentally or on purpose. You won’t usually be able to tell the intent of a malicious OAuth connection, but it’s one indicator that a cloud account takeover has occurred. It’s best to err on the side of caution when you detect a risky or malicious OAuth connection and take a deeper look into an account’s other activity to try to determine if it’s indeed compromised or if it was simply an unsuspecting employee.
How are malicious apps used by cyber criminals? There are several ways, but the most common is to help them send lateral phishing emails. A hacker can create an application that requires read, write, and send permissions for a user’s Gmail or Outlook 365 account. Once granted that permission through OAuth, they can then send emails containing phishing links directly through the users account. Without ever needing to login to the account they’ve hijacked! And, again, these types of emails go completely undetected by traditional phishing filters and MTAs that your district is already using.
If you do detect a risky or malicious OAuth connection in your cloud environment, the best first step is to remove the connection. Then, you should get in contact with the person whose account it was connected to to ask if they’d added the app. If they didn’t add it themselves, you should initiate a password reset on the account immediately and run an audit to see if any files or other accounts have been compromised.
5. Abnormal File Sharing & Downloading
Sometimes, when a cloud account takeover occurs, the objective is to get as much information as possible. This is particularly true for accounts that have been granted access to sensitive or proprietary information. This type of information can include social security numbers, names, addresses, and phone numbers, health information, financial information, and intellectual property.
If your cloud security platform detects that an account is sharing sensitive information outside of the district’s domain (or attempting to) or that it’s downloading that information, it could be an indication of a compromised account. You will want to immediately lock that account down, and then force a password reset and audit the rest of your environment to see what was impacted and if any other accounts may be compromised.
Cloud account takeovers are difficult to detect for admins using traditional security tools to solve cloud security issues. Using a cloud security platform to monitor, detect, and automate responses to these five account takeover indicators makes life much easier. And it makes data stored in the cloud far more secure. If your school district is using cloud applications for email, file sharing, storage, etc. it’s time to start taking your cloud data security more seriously. Claim your FREE Google/Microsoft 365 security audit today and make sure your accounts haven’t been compromised.

