How it works
Google Workspace & Microsoft 365 cloud security platform for K-12 IT teams
Prevent data breaches and detect student safety signals in district cloud apps
How it works
Cloud Monitor seamlessly integrates with your district’s cloud applications, such as Google Workspace and Microsoft 365. Once connected, our platform continuously monitors user activity, files, and emails in real-time.
API-based cloud security platform doesn't require a browser extension, proxy, agent, gateway, or virtual appliance
Continuous visibility and control across your school district's cloud applications, and the data stored in them
Automate policy enforcement with out-of-the-box and customizable policies, so your district's data is secure while you focus on other priorities
Lightning fast policy enforcement and alerts without causing network delays that impact work and classroom learning experiences
Easy to set up, easy to manage.
Cloud Monitor is a cloud security platform designed to make managing Google Workspace and Microsoft 365 security easy for IT leaders and system admins in K-12 school districts. It doesn't require hardware or on-site installations, proxies, or browser extensions. The platform takes minutes to activate, requires no special training, and has no impact on users or networks.
Data Security
Student and staff information stored in school information systems are lucrative targets for cybercriminals. At the same time, the most common cause of school data incidents is a simple accidental exposure. District IT teams must be able to manage access to sensitive information stored in Google Workspace and Microsoft 365 not only to comply with state and federal regulations but also to protect students and staff.
- Automate data loss prevention to protect social security numbers, W2s, payment and health information, and more
- Detect anomalous events that indicate unauthorized access to data
- Identify when data is being improperly emailed or shared
- Continuously monitor behavior in Google Workspace and Microsoft 365 and automatically mitigate data security risks
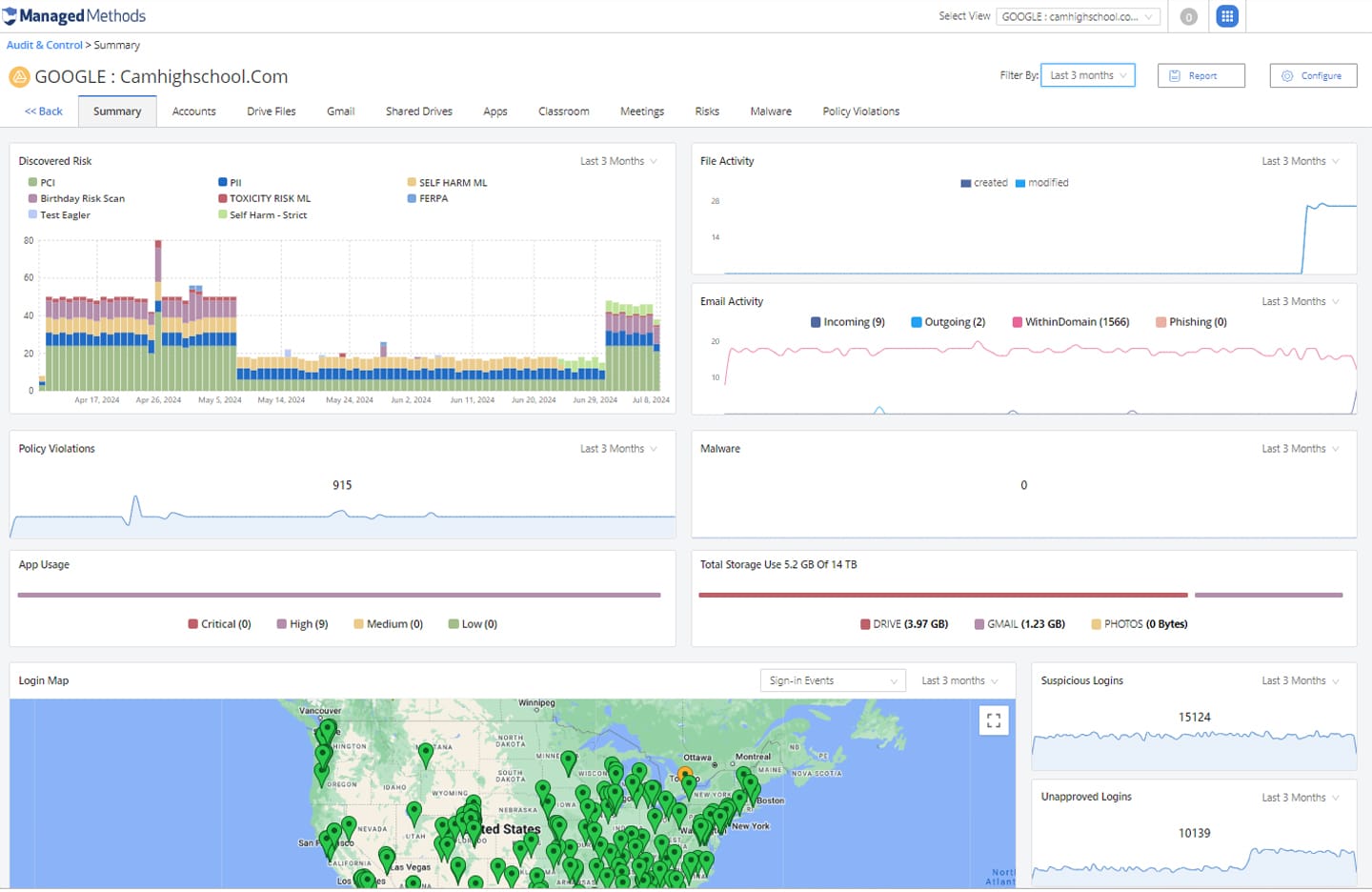
Phishing & Malware Threat Protection
Phishing is still the #1 threat vector used by criminals to gain access to school user accounts. At the same time, schools are experiencing a sharp increase in malware—including ransomware—attacks. If your district uses Google Workspace and/or Microsoft 365, external threats can gain access to student and staff information through email, file sharing, and risky 3rd party SaaS apps.
- Scan internal & external emails for phishing and malware threats in the message body, attachments, and links
- Automatically quarantine or delete emails and shared files containing phishing and malware links
- Identify risky 3rd party SaaS applications connected to district Google and Microsoft accounts through OAuth
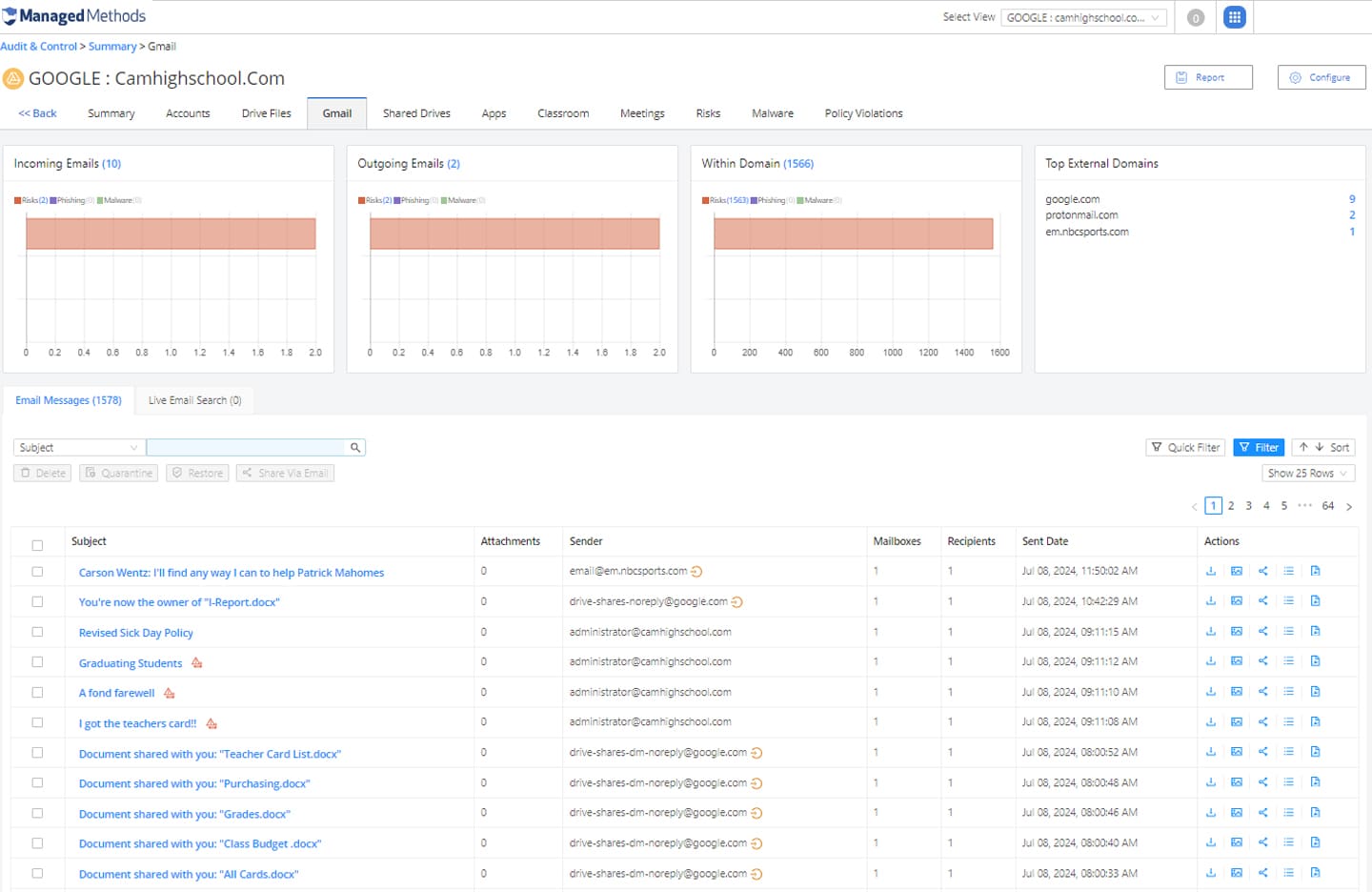
Prevent Account Takeovers
Phishing and malware attacks can lead to account takeover of your district’s Google Workspace and/or Microsoft 365 accounts. An account takeover is notoriously difficult to detect in cloud applications and can lead to additional cyber risks and data exposure.
- Protect district Google Workspace and Microsoft 365 from an account takeover with advanced phishing and malware threat protection build for the cloud
- Easily detect behavior that indicates an account takeover attack is underway, such as multiple unsuccessful logins, logins from foreign locations, and failed multifactor authentication checks
- Automatically detect and remediate successful account takeovers using highly customizable policy enforcements
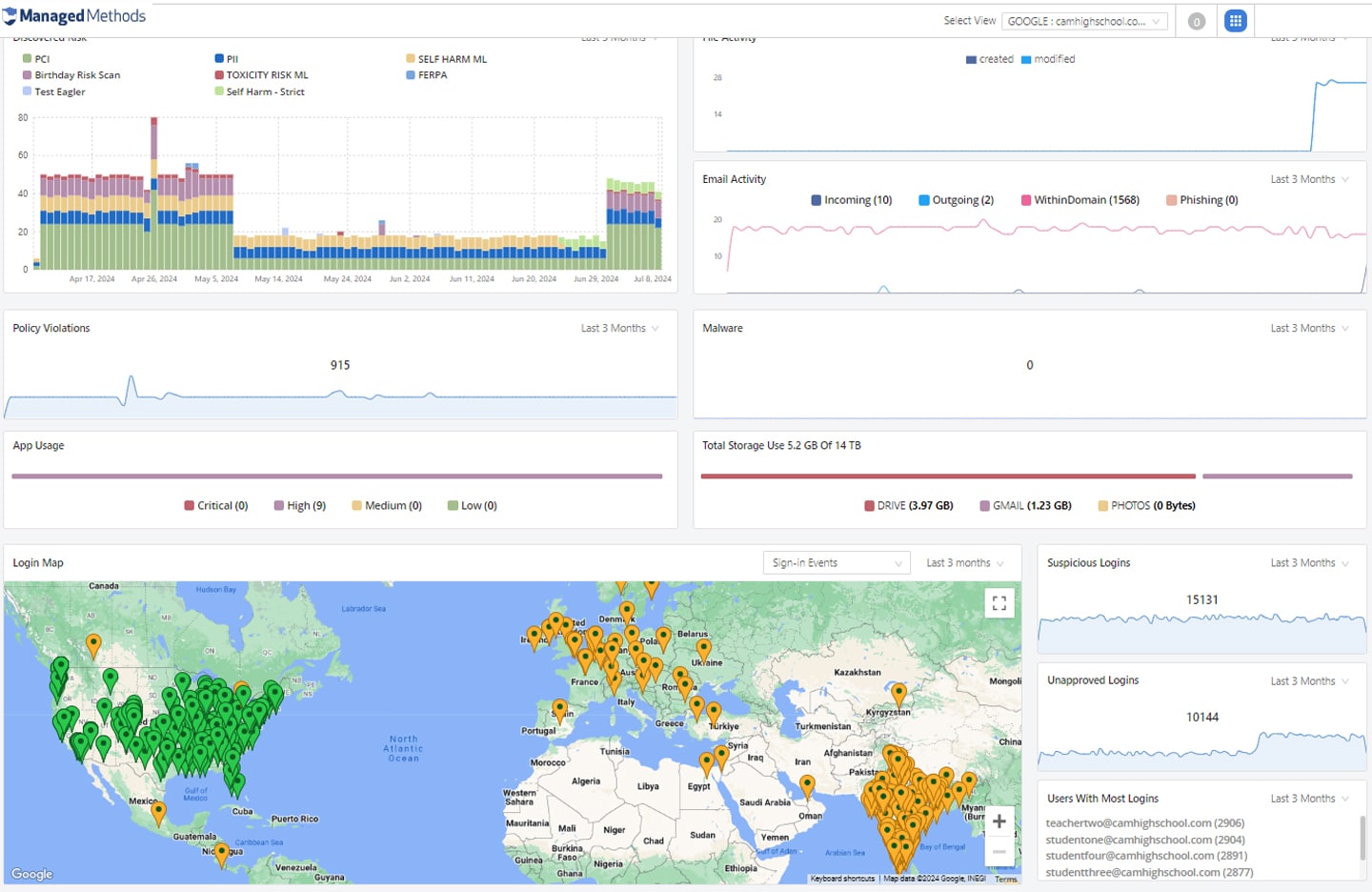
Monitor Safety Signals
Monitor student safety signals in Google Workspace and Microsoft 365 using artificial intelligence (AI) and keywords scanning in emails, files, drives, and shared drives to detect red flags in text and image content.
- Deep, 1:1 API integrations monitor district Google Workspace and Microsoft 365 accounts 24/7/365 without the need to collect or store any personalized data
- AI and keyword scanning detects self-harm, cyberbullying, threatening, and explicit content and alert school administrators
- Detailed incident information, including the document owner, contributors, text history, sharing history, and more
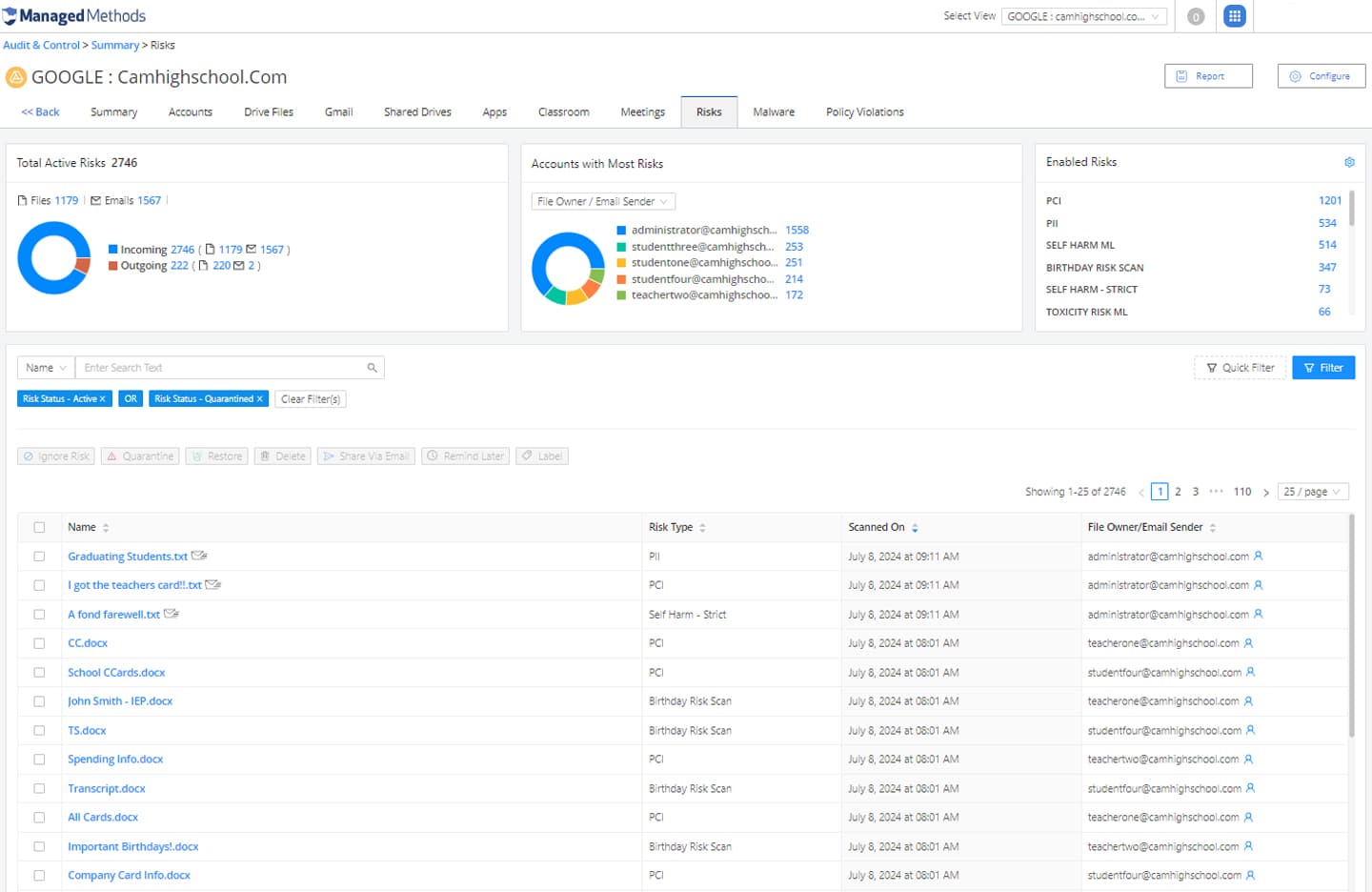
- Activate cloud data security
- Full support for BYOD and 1:1 models
- Automatic account activity
- Easy incident remediation and reporting
- No delays or impact on end users
Committed to Student Data Privacy








Frequently asked questions
Whether you’re curious about our platform’s functionality, deployment process, or support offerings, our FAQ provides comprehensive information to address your queries.
Is ManagedMethods FERPA, COPPA, and CSPC compliant?
Yes! ManagedMethods’ Cloud Monitor platform is certified FERPA, COPPA, and CSPC compliant by iKeepSafe. We’re also a member of the Student Data Privacy Consortium, a Student Privacy Pledge signatory, and a Consortium for School Networking (CoSN) cybersecurity initiative sponsor.
At ManagedMethods, we take our product infrastructure security very seriously, which is why we built the platform on Google Cloud Platform (GCP).
We also take your data security and student data privacy very seriously. ManagedMethods DOES NOT copy, backup, or retain customer data. Nor does its employees have any access to customer data, except when granted explicit permission in the context of a support ticket. All customer support employees who may view or access information in this context are required to pass a background check.
Both of ManagedMethods’ products, Cloud Monitor and Content Filter, use deep, 1-to-1 API integrations to provide visibility and control of your districts cloud computing and Internet browsing behavior.
Cloud Monitor scans data and detects risks within your Google Workspace and/or Microsoft 365 environment. The platform works as a nearly native tool to report on and remediate data security, student safety, and compliance risks within your cloud environment.
Content Filter uses a browser extension, deployed through Google Admin console, to block or allow access to specific websites and/or site categories based on your policy configuration. It also uses AI, compressed on users’ browsers, to provide districts with technologically advanced safety monitoring which deploys lightning fast alerts without slowing down the browsing experience.
You can read our publicly available Privacy Policy and Terms of Service any time at your convenience.
Is Cloud Monitor a content filter?
No, Cloud Monitor is not a content filter. The platform does not block access to websites, domains, and other types of content. However, we are happy to announce the availability of our new, innovative Content Filter product, which you can learn more about here.
Cloud Monitor scans your district’s Google Workspace and/or Microsoft 365 domain to detect content based on specific parameters (we call “risks”) that are set up using contextual keywords, regex text, and numerical strings, and artificial intelligence. Cloud Monitor is capable of scanning for different types of content within your domain for both data security and student safety use cases.
For example, it can detect when a file containing personally identifiable information is being shared outside your domain and/or globally and automatically break the share. The platform can also detect when explicit images are being uploaded and/or shared from your district’s shared drives, email, and chat apps.
Cloud Monitor specifically works to detect risks inside Google Workspace for Education apps currently including Gmail, Drive, Shared Drive, Docs, Slides, Sheets, Chat, Meet, and Classroom. In Microsoft 365, the platform works to detect risks inside Microsoft’s cloud-specific environment (not on-prem software), including Outlook, Word, PowerPoint, Excel, SharePoint, and OneDrive.
To learn more about the K-12 cyber safety and security layers, and how Cloud Monitor fits within them, read more here.
Is Cloud Monitor a firewall / next-gen firewall?
No, Cloud Monitor is not a firewall or next-gen firewall in the literal, technical sense. Cloud Monitor will not block anything from coming into or leaving your domain. The platform technology does not use any agents, proxies, gateways, or extensions to block or filter traffic. It is not perimeter-based security.
Cloud Monitor uses deep, 1-to-1 API integrations with Google Workspace and Microsoft 365 to provide a layer of monitoring and control security within your district’s cloud applications. In most cases, the platform will detect and remove, revoke access, or quarantine risks (based on your policy configurations) within seconds, oftentimes before any human realizes that the email or file share has come across.
This is particularly important when it comes to our phishing and malware remediation in email (Gmail and Outlook 365). While Cloud Monitor won’t technically block an email, it will remove it from your inboxes and quarantine suspicious emails at a rate of mere milliseconds. Many of our customers have noted phishing and malware emails that Cloud Monitor catches that their native Gmail phishing filters and third-party MTAs did not.
In short, Cloud Monitor protects your data stored, accessed, and shared in cloud applications instead of your perimeter. This is a vital security layer for districts using cloud applications and is also critical to building a zero-trust security model.
Learn more about the differences between Cloud Monitor cloud security and firewalls here.
What is cloud security and how is it different from my current network security setup?
Most network security configurations today rely on perimeter-based security infrastructure. This means that, if you don’t have cloud security protections in place, your current security setup likely relies heavily on perimeter security technology, such as firewalls and mail transfer agents (MTAs). While this level of security is important to your overall cybersecurity infrastructure, it’s not the whole picture.
If your district is using cloud-based applications such as those provided in Google Workspace and/or Microsoft 365 (including Gmail, Google Docs, Google Drive, Exchange Online, SharePoint, OneDrive, etc.) you need a cloud security layer to protect access to data and accounts beyond where firewall technology can reach.
We sometimes liken the differences to going to a bar. On a busy Saturday night, most bars will have a bouncer (or two) at each door to check IDs, aggressive behavior, etc. to limit access to the inside only to those who should be authorized to be let inside. But once someone gets inside, the bouncer at the door is no longer helpful. Someone could get in with a fake ID and start causing trouble once inside. That’s why bars will also have security inside the bar, to make sure those that have been granted access are behaving appropriately.
Learn more about the differences between Cloud Monitor cloud security and firewalls here.
Does ManagedMethods retain any data?
ManagedMethods DOES NOT copy, backup, or retain customer data. Nor does its employees have any access to customer data, except when granted explicit permission in the context of a support ticket. All customer support employees who may view or access information in this context are required to pass a background check.
Both ManagedMethods products, Cloud Monitor and Content Filter, use deep, 1-to-1 API integrations to scan data and detect risks. Cloud Monitor works within your district's Google Workspace and/or Microsoft 365 environment. The platform works as a nearly native tool to report on and remediate data security, student safety, and compliance risks within your cloud environment. Meanwhile, Content Filter works on the browser level to ensure CIPA compliance on the internet.
You can read our publicly available Privacy Policy and Terms of Service any time at your convenience.
How is Cloud Monitor different from Google’s native security?
First, it’s important to know that ManagedMethods is a proud Google Cloud and Google for Education Partner. Both Cloud Monitor and Content Filter platforms are built on Google Cloud Platform (GCP) because it is the world’s most secure and best-performing cloud infrastructure platform. So, it’s safe to say that we’re really big fans of Google and the products the company provides.
The short answer to this question is that Cloud Monitor is far more user friendly than Google’s Admin console. This is the main bit of feedback that we get from our customers every day, whether they are on the free version of Google Workspace for Education (Fundamentals) or are Google Workspace for Education Plus licensees.
Because Cloud Monitor integrates with Google Workspace through APIs, the platform is reporting on information that exists within your Google Workspace environment. The main difference is that we’re organizing the data in ways that are far easier to find and analyze. We’re also doing all the “heavy lifting” on the back end to automate alerts and actions so you don’t need to expend your limited resources on creating scripts and coding.
Some additional, high-level differentiators between Cloud Monitor and Google Admin console include:
- Cloud Monitor allows admins to make deeper investigations and analysis of data security issues without the need for scripting. It also allows admins to remediate policy violations without the need to upgrade to Google Workspace for Education Plus (though some of our customers choose to in order to take advantage of other Plus benefits for students and teachers).
- ManagedMethods takes student safety monitoring very seriously. We’ve worked closely with our customers to develop out-of-the-box safety monitoring policies and artificial intelligence trained specifically for the K-12 environment. While admins could, in theory, set up Google DLP policies in Admin console to scan for keywords in similar ways that Cloud Monitor does, it doesn’t provide quite the same level of functionality and customization. Admin console also doesn’t provide any kind of student safety monitoring templates in their policy library or AI in their safety monitoring technology.
- With Cloud Monitor, you get dedicated, hands-on customer success support. Any time you have an issue or a question, our team is quick to respond and do what we can to fix the issue or answer your questions. You’re not lost in a sea of millions of users—doing what we can to make your life easier truly matters to us.
- Districts that use both Google Workspace and Microsoft 365 for Education experience even more value, because Cloud Monitor provides visibility and control over both environments from a single platform.
Learn more about the differences between Cloud Monitor and Google Admin console's security features here.
How is Cloud Monitor different from Microsoft’s native security?
First, it’s important to know that ManagedMethods is a proud Microsoft for Education Partner. We work closely with the Microsoft partner team to ensure that our platform is as beneficial to Microsoft 365 customers as possible.
The short answer to this question is that Cloud Monitor is far more user friendly than Microsoft’s Security & Compliance Center. This is the main bit of feedback that we get from our customers every day, no matter which Microsoft 365 for Education level they’ve licensed.
Because Cloud Monitor integrates with Microsoft 365 through APIs, the platform is reporting on information that exists within your Microsoft 365 environment. The main difference is that we’re organizing the data in ways that are far easier to find and analyze. We’re also doing all the “heavy lifting” on the back end to automate alerts and actions so you don’t need to expend your limited resources on creating PowerShell scripts and coding.
Some additional, high-level differentiators between Cloud Monitor and Microsoft 365 Security & Compliance Center include:
- Cloud Monitor allows admins to make deeper investigations and analysis of data security issues without the need for PowerShell or any kind of scripting. It also allows admins to remediate policy violations without the need to upgrade to an A5 level or purchase security and compliance add-ons.
- ManagedMethods takes student safety monitoring very seriously. We’ve worked closely with our customers to develop out-of-the-box safety monitoring policies and artificial intelligence trained specifically for the K-12 environment. While admins could, in theory, set up DLP policies in the Security & Compliance Center to scan for keywords in similar ways that Cloud Monitor does, it doesn’t provide quite the same level of functionality and customization. Microsoft’s Security & Compliance Center also doesn’t provide any kind of student safety monitoring templates in their policy library or AI in its safety monitoring technology.
- With Cloud Monitor, you get dedicated, hands-on customer success support. Any time you have an issue or a question, our team is quick to respond and do what we can to fix the issue or answer your questions. You’re not lost in a sea of millions of users—doing what we can to make your life easier truly matters to us.
- Districts that use both Microsoft 365 and Google Workspace for Education experience even more value, because Cloud Monitor provides visibility and control over both environments from a single platform at not additional charge.
Learn more about the differences between Cloud Monitor and Microsoft’s Security & Compliance Center here.
How does Cloud Monitor work?
Cloud Monitor uses deep, 1-to-1 API integrations to scan data and detect risks within your Google Workspace and/or Microsoft 365 environment. The platform works as a nearly native tool to report on and remediate data security, student safety, and compliance risks within your cloud environment.
Cloud Monitor comes with out-of-the-box risk and policy templates that can get your district on the path to better cloud security and student safety monitoring right away. The platform also allows you to edit the out-of-the-box templates and/or create your own to make the platform work best for your specific needs and context. We currently provide extensive customer success and solutions support at no additional cost to our customers.
Because Cloud Monitor uses APIs, instead of appliances, in most cases the initial setup and activation takes mere minutes. While it may take a bit of time to get the platform configured to your liking, many of our customers find that they are accessing the product settings less and less over time, as automated policies take over much of the repetitive remediation work.
Further, due to the API-based architecture of the platform, Cloud Monitor will work in the same way to monitor, audit, and control data security, student safety, and compliance risks in your district’s Google Workspace and/or Microsoft 365 environment no matter what device and/or network a student, teacher, or staff member is accessing your domain from.
What do PCI and PII stand for?
PCI stands for Payment Card Industry and specifically refers to payment card information. Merchants (including school districts) that process and/or retain payment card information must comply with PCI Security Standards to ensure they aren’t putting consumer data at risk.
PII stands for Personally Identifiable Information and refers to any information that can be used to identify a specific individual. PII can include a person’s name, social security number, physical address, email address, user name, passwords, tax information (such as W2s), bank account information, and more.
It’s important to note that “social engineering” campaigns are more popular among cybercriminals who take the long-game strategy to collect bits and pieces of PII on individuals over a longer period of time, eventually using collected information to orchestrate a larger attack.
How does Cloud Monitor help me manage files/data being improperly shared outside my domain?
Cloud Monitor makes it easy to see what files are being shared inside and outside your domain, via link, and via global permissions. Admins can also see the number of users the file is shared with, and further dive into specifically which users/email accounts the file is shared with—categorizing internal and external domain shares.
Cloud Monitor will help you manage files/data being improperly shared outside your domain in a couple of ways. Admins can begin by unsharing files/data that are improperly shared outside your domain on either a one-off or bulk files unshare basis.
Admins can also use risks and policies to automate unsharing files that are improperly shared outside the domain. Cloud Monitor provides a number of out-of-the-box risks and policies to accomplish this, including social security numbers, credit card numbers, and FERPA violations. Admins can edit these provided risks and policies, as well as create their owner risks and policies from scratch.
Cloud Monitor will scan both text and image files to determine if a shared file triggers any configured risk and/or violates a policy.
See for yourself! Check out our Cloud Monitor demo on-demand video here.
How does Cloud Monitor scan for malware?
Emails and files are scanned using a service called Cylance which not only scans files and compares against the database of known malware, but also analyzes the data structure and file behavior to detect suspicious activity and can help prevent attacks before they are known to be malicious.
Where do quarantined files go?
When you quarantine a file in Cloud Monitor, it is removed from the file owner’s Drive/OneDrive and all shares to the file are broken. The file is moved to a folder in the Cloud Monitor admin’s Drive/OneDrive named "CAM_Quarantine" on the administrator's cloud drive for further investigation. Administrators can get to the quarantined file by navigating to their Drive/OneDrive account and opening the CAM_Quarantine folder.
Where do quarantined emails go?
When you quarantine an email, it is moved to the user's trash folder. Alternatively upon request quarantined emails can be sent to spam.
Cloud Monitor also makes it easy to “un-SPAM” emails in just a few simple clicks. This need became particularly important for school districts using Google Classroom and other LMS tools. Some wily students think it’s funny to mark email notifications from their teachers as SPAM. Using Cloud Monitor, admins can easily find and “un-SPAM” any emails they need to.
Admins can automate un-SPAMing emails by setting up SPAM email exclusions for regularly mis-mark messages. The process includes defining email subject lines that you would like to be automatically moved back into the user's inbox from their SPAM folder.
Will I get a lot of false positives?
False positives are, unfortunately, part of the territory when it comes to this type of technology. We have heard anecdotally from our customers that they get way less false positives from Cloud Monitor than other, similar solutions. That being said, we do not guarantee a specific level of false positives (or lack thereof).
We do work hard to make adjustments to risk configurations and machine learning model training based on our customers’ false positives feedback. Customers can report false positives by either sending an email to our support team or directly in the platform using a “Report False Positive” button.
Can Cloud Monitor help me find and control 3rd party apps?
Yes! In fact, our customers find Cloud Monitor's 3rd party apps auditing reports to be much more useful than native Google and Microsoft admin reports and controls.
Using Cloud Monitor, admins can find which 3rd party apps are connected to their domain through OAuth, and specifically which user(s) and Organizational Unit(s) that have connected the apps. Admins can also see app information such as app category, permission scopes, risk level (low, medium, high, and critical), the percentage of other Cloud Monitor customers who have sanctioned the app, and the number of OUs and users that have activated the app. Admins can then individually or bulk remove, sanction, unsanction, warn the user(s), and/or share via email multiple apps at a time.
Further, admins can set up app policies to automatically detect certain apps and take the desired action to remove, unsanction, and/or warn the users when a 3rd party OAuth app is granted access to your domain (Google only).
Can Cloud Monitor help me find and control unapproved browser extensions?
It depends. Because Cloud Monitor is an API-based platform, it does not currently have the ability to detect or control all types of browser extensions. However, if the extension is enabled through an OAuth token, Cloud Monitor will be able to detect it, just like it does with OAuth 3rd party apps connected to your domain.
What’s the difference between risk and policy?
A risk is set up to tell the Cloud Monitor platform what you want it to look for as it scans your Google Workspace and/or Microsoft 365 domain. You may find a wide variety of risk types in your domain. Common risk types include (but are not limited to) image risks, profanity, PII, and PCI. Risk types can be customized in Cloud Monitor to ensure you only see the risks that are relevant to you. Risks can be set up using comma-delimited keyword lists, and regex strings. They can also be further refined based on the risk match count, context, and context check length.
Policies are used to automate the actions you would like the platform to take when a risk is detected in your environment. In Cloud Monitor, policies are divided into three categories for Google Workspace domains: content policies, user policies, and app policies. They are divided into two categories for Microsoft 365 domains: content policies and user policies.
Depending on the policy category, you can customize automated remediation based on the risk, the source of the risk (such as email, shared file, etc.), the sharing behavior by domain, OU, and/or a specific user. Depending on the type of risk and policy, you can remediate the risk in a number of different ways, including (but not limited to): unshare, quarantine, delete, remove from your domain, revoke access to your domain, sanction, unsanction, and warn the user.
Can I define my own risks?
Yes! Cloud Monitor comes with out-of-the-box risk definitions to get you started. You can choose to edit these risks however you need to. You can also create your own risks at any time!
Can I define my own policies?
Yes! Cloud Monitor comes with out-of-the-box policies to get you started. You can choose to edit these policies however you need to. You can also create your own policies at any time!
What is the end user experience when a policy violation occurs in Cloud Monitor?
That largely depends on how you sent up your policies and user notifications in Cloud Monitor. In most cases, admins will choose to send an automated email notification to the end-user who violates a policy, explaining the reason for the policy violation and what (if any) additional actions they need to take. These emails are easily customized in the Cloud Monitor platform.
In the case of student safety policies, such as monitoring for self-harm signals, most districts choose not to automate user notifications in Cloud Monitor. Instead, they may send a notification to a school counselor or principal who is trained in taking the next steps to follow up with the student in distress.
Can Cloud Monitor help me “un-SPAM” emails?
Yes! Cloud Monitor makes it easy to “un-SPAM” emails in just a few simple clicks. This need became particularly important for school districts using Google Classroom and other LMS tools. Some wily students think it’s funny to mark email notifications from their teachers as SPAM. Using Cloud Monitor, admins can easily find and “un-SPAM” any emails they need to.
Admins can automate un-SPAMing emails by setting up SPAM email exclusions for regularly mismark messages. The process includes defining email subject lines that you would like to be automatically moved back into the user's inbox from their SPAM folder.
Is there a way to automate tasks in Cloud Monitor so I don’t have to “babysit” it?
In most cases, yes! Cloud Monitor comes with out-of-the-box and customizable policies that allow the platform to take remediative action, send notifications to users who violate policies, and/or send policy violation alerts to admins.
Your automation set up can be as simple or as comprehensive as you need it to be to make your work day a bit less hectic.
Can Cloud Monitor stop an email from being sent if it violates a policy?
No. Because Cloud Monitor is an API-based platform, it does not sit “inline” and therefore does not block any traffic. A policy can be set up to notify the admin, user, and/or any other role when an email is sent that violates any policies that have been created in the platform. Additionally, if the email contained a sharing link to a file in your district’s Google Workspace and/or Microsoft 365 domain, a policy can be set up to revoke the sharing of that file. Sharing revocation happens in near real-time in this case.
Can Cloud Monitor stop a file from being downloaded if it violates a policy?
No. Because Cloud Monitor is an API-based platform, it does not sit “inline” and therefore does not block any traffic—this includes downloads. A policy can be set up to notify the admin, user, and/or any other role when file download behavior violates any policies that have been created in the platform. Notification when a policy is violated happens in near real-time. A policy can also be created to change the password or suspend the account when such a download policy is violated, which also happens in near real-time.
How does Cloud Monitor help me manage my devices?
Cloud Monitor is not meant as a device management platform. It currently does not do anything to help you manage your devices in any way. Our focus is on monitoring and providing total control over your Google Workspace and/or Microsoft 365 environment.
Does Cloud Monitor monitor student social media accounts?
Cloud Monitor does not in any way monitor student social media accounts. Cloud Monitor only monitors and controls activity within the school district Google Workspace and/or Microsoft 365 domains.
Our Content Filter product, on the other hand, can help you control access to social media websites and flag inputs that might indicate a student safety risk.
Can Cloud Monitor help my team identify Google Docs, Slides, etc. that are being used as chat rooms?
Yes! This is a common and popular use case among our customers. Cloud Monitor can be configured to use its risks and policies engines to monitor for and alert admins on improper text and images being shared in Google Workspace for Education apps including Gmail, Google Docs, Google Slides, and Chat. The platform works the same way in Microsoft 365 apps including Outlook, Word, and PowerPoint.
Can Cloud Monitor help my team detect self-harm signals in student accounts?
Yes. This is an unfortunately common and popular use case among our customers. Cloud Monitor can be configured to use its risks and policies engines to monitor for and alert admins on improper text and images being shared in Google Workspace for Education apps including: Gmail, Google Docs, Google Slides, and Chat. The platform works the same way in Microsoft 365 apps including Outlook, Word, and PowerPoint.
Self-harm risks can be set up using customizable keyword and regex risks, as well as our proprietary AI-powered Safety Signals.
How long does Cloud Monitor take to deploy?
Because Cloud Monitor uses APIs, instead of appliances, in most cases the initial setup and activation takes mere minutes.
While it may take a bit of time to get the platform configured to your liking, many of our customers find that they are accessing the product settings less and less over time, as automated policies take over much of the repetitive remediation work.
What is the setup and management resource commitment for Cloud Monitor?
Setup and management looks very different for different school districts. The time and resource commitment depends on a variety of factors, including but not limited to the number of users you have in your domain, the amount of files, emails, and chats that need to be scanned initially, and the variety and sensitivity of your data files.
Because Cloud Monitor uses APIs, instead of appliances, in most cases the initial setup and activation takes mere minutes. Then, depending on the volume of data in your domain, we typically wait two to seven days for the platform to do it’s initial scan. During this time, Cloud Monitor is scanning all files, emails, chats, etc. that have been created, sent, shared, and/or edited in your environment over the past 30 days.
When you first activate your 30-day free trial, we like to schedule a kick-off call with the person/people on your team who will be using the platform to do an initial review of your data and the risks that were discovered. During this time, a member of our customer success team will walk you through the platform and address any questions, concerns, and edits to risks and policies you might like to make at this point.
While it may take a bit of time to get the platform configured to your liking, many of our customers find that they are accessing the product settings less and less over time, as automated policies take over much of the repetitive remediation work.
Our customer success and solutions engineering team are always available to help you get your Cloud Monitor instance configured just right! From the time you start your 30-day free trial through the life of your partnership with us, our team is committed to helping make your life (or at least your work) easier.
Can I add additional users to my Cloud Monitor account?
Yes! Additional users can be added to your Cloud Monitor account at any time and at no additional cost. Breaking out users into separate roles is part of our Advanced licensing and comes at an additional cost.
Can I delegate different tasks in Cloud Monitor to different people on my team/in my district?
Yes! You can add additional users to your Cloud Monitor platform instance, and even control what views and settings they have access to in different roles configurations.
What is the licensing model for Cloud Monitor?
Cloud Monitor is licensed on a per-user account basis over a one year term. Multi-year discounts are available for school districts with large user account sizes. Please contact sales for additional information regarding licensing and pricing for your school district.
Contact sales to learn more about licensing.
How much does Cloud Monitor cost?
Cloud Monitor is purchased on a flat-rate, per user account basis, calculated based on the number of employee and student accounts in your district’s domain. There is no additional charge for districts that use both Google Workspace and Microsoft 365.
Cloud Monitor does offer advanced features at an additional cost including malware scanning, advanced role notifications, and enterprise-level support.
Contact sales to learn more about pricing.
What other school districts are using Cloud Monitor? Can I talk with them?
Our Customer Stories are a great place to start learning about how other school districts are using Cloud Monitor.
When we get further along in our relationship, we are more than happy to connect you with customers who can answer your questions.
Do you provide a free trial?
Yes! We offer any new potential customer a 30-day free trial. Set up and activation typically takes a few minutes (though, usually a bit longer for Microsoft 365 domains). Our platform is connected to your domain via APIs, so there is no impact on your domain, data, or network when you activate with Cloud Monitor, nor when you deactivate if you choose not to move forward.
We feel that we have to warn you: once you experience Cloud Monitor it is going to be very difficult for you to go back to life before it. Over 70% of school districts who activate their 30-day free trial become full customers. Consider yourself warned 🙂
Click here to request your 30-day free trial.
How do I get in contact with someone to schedule a demo and get more information?
We’d love to hear from you! Please click here to request a demo. A representative for your state/province will be in touch with you shortly to schedule a time that works best for you.
Testimonials
Customer success stories
“When I first learned about ManagedMethods I was skeptical that such an inexpensive solution would be able to secure our Google Workspace data better than Cloudlock. However, after our first week using the solution, I was more than convinced. Cloud Monitor has been one of the best technology decisions I’ve made this year.”
Ed Newman
CSO & Director of Technology Services ESC 12, TX
“The addition of ManagedMethods to our IT infrastructure allows me and my team to feel confident about protecting our students and staff when using Google Workspace. The dashboard and alerts provide me real-time info so that I can take immediate action to thwart any threats.”
Steve Bartlett
Technology Director, Bremerton School District, WA
“ManagedMethods’ solution provided us a level of visibility we needed to ensure the security and safety of our students and staff. The solution was quick to deploy and gave us immediate insights.”
Tim Miles
Director of Technology, Steamboat Springs School District, CO
Leaders in K-12 Data Security & Cyber Safety



































































Contact us
Take proactive steps to safeguard your valuable data
Start now to fortify your defenses and safeguard your digital assets.
