Get cloud security like you’ve never experienced before with CASB 2.0
CASB 2.0 is the natural evolution of cloud security technology that was born as the cloud revolution has aged into common practice. No longer is a cloud-enabled workforce a key differentiator, nor does it provide significant strategic advantage. Companies and organizations for all types and sizes have made the switch to cloud computing, and those that haven’t are now more the outlier. But the big question now is: how are cloud applications being secured?
This question was answered with the CASB. What is CASB? It’s a term coined by Gartner, and abbreviated from cloud access security broker. The term is used to describe the cybersecurity industry segment of tools designed to secure access to information stored in cloud applications. Initially, CASB vendors provided solutions that rely heavily on network security fundamentals like firewalls, proxies, and web gateways.
But, as more and more data storage and access traffic is routed through cloud applications, the perimeter has been declared all but dead. Open access to data from any device, in any location requires a different kind of solution that doesn’t just secure cloud access “at the border”, but monitors and controls activity within cloud applications themselves to support zero trust security models. Thus, CASB 2.0 was introduced to the market…
The CASB API Revolution
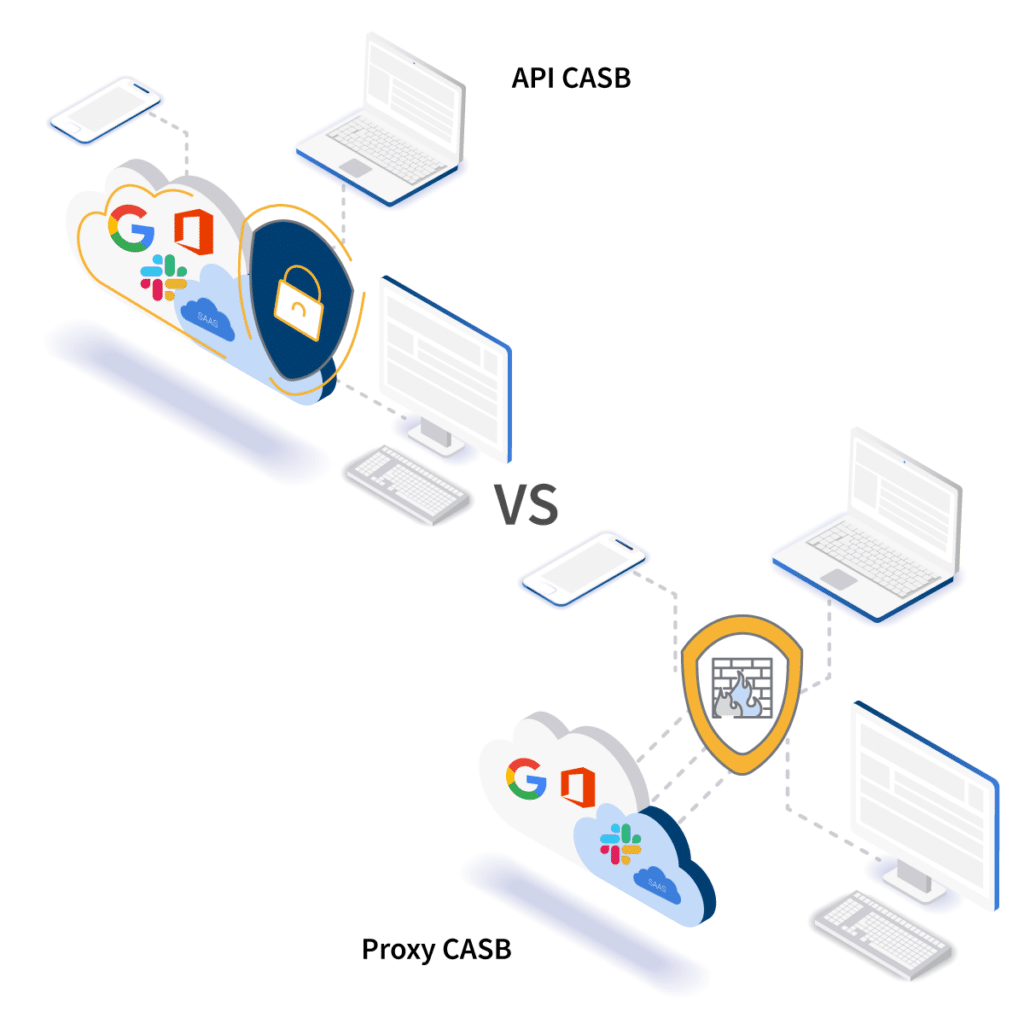
After a few years of trying to fit network security technology into cloud security models, someone had the bright idea to use APIs in their CASB architecture. And CASB 2.0 was born.
Using API vs proxy technology to secure cloud applications is a natural choice for CASB 2.0. It uses the native integrations protocols to secure access to data stored within the application, as well to control activity. Rather than placing an appliance between employees and the files they are trying to access, API-based CASB 2.0 provides a fast, seamless, and secure experience for end users and IT teams alike.
Most organizations already have a firewall or a secure web gateway (SWG). Legacy CASBs that use proxies (either forward, reverse, or “agentless”) simply duplicate this layer in your cybersecurity infrastructure. CASB 2.0 uses APIs to protect your data stored in the cloud, rather than your perimeter. In this way, CASB 2.0 is an additive security layer, rather than a duplicative one. They will work very well with existing security tools, including firewalls, SWG, MTAs, etc. to help security teams gain an increased level of visibility and control over what is going on within their cloud applications.
CASB 2.0 builds deep, 1-to-1 API connections between the CASB platform and the cloud application that needs to be secured. If your organization uses G Suite, Office 365, Slack, and Dropbox, for example (like many do) you would, in effect, have a Microsoft CASB, a Google CASB, a Slack CASB, and a Dropbox CASB. All wrapped up into one, easy to use and manage platform!
What Does CASB 2.0 Solve?
Using a CASB solves a number of business challenges. CASB 2.0 that uses an application’s native APIs to secure, monitor, and control activity within it takes it a step further. Advanced protection and control features that CASB 2.0 provides includes:
Discover & Control Shadow Cloud IT
Shadow IT has long been the crux of cybersecurity controls. The emergence of cloud-based SaaS applications has only made it more of an issue. OAuth applications, in particular, can cause huge problems for security teams and organizations. CASB 2.0 shines a light on OAuth shadow cloud IT. And it provides advanced controls over it, including ranked risk factors, automatic unsanctioning, deletion, etc.
Advanced Data Loss Prevention
Data loss prevention is a broad topic, complicated further by the amount of data being stored and accessed in the cloud. Inappropriate sharing settings, employee downloads, and more are issues that IT and SecOps teams can gain control of in the cloud with CASB 2.0.
Shut Down Account Takeovers
Account takeovers are a growing concern for organizations. It is easier for criminals to gain access to even more information when they are able to takeover cloud application accounts. CASB 2.0 provides granular visibility and control over activity taking place within cloud applications. This means that, if an account takeover gets past your perimeter and is successful, your CASB security will be able to detect anomalous behavior, such as external sharing attempts, mass downloads, sending phishing emails from internal accounts, etc. The platform can then take remediation actions when it detects such behavior, including shutting out the account entirely and forcing a password reset.
Advanced Malware & Phishing Protection
Malware and phishing schemes have evolved in the cloud, and are now including lateral phishing tactics that cannot be detected by traditional MTAs or SWGs. Lateral phishing starts with an account takeover, sending phishing emails from within the organization to others in order to gain access to more information. Like account takeovers, this type of attack is notoriously difficult to detect and stop without a CASB solution in place.
The world of doing business has evolved dramatically in a very short amount of time. Cloud computing has driven so much innovation and improvement during that time, and has been a boon for businesses and organizations of all types and sizes. Unfortunately, many organizations have not taken the time to understand the nuances of securing information in the cloud in the same way they have network security.
The result is a lingering myth that network security technology is sufficient to secure cloud applications. Teams that are taking their cybersecurity infrastructure seriously are using CASB 2.0 technology to secure the data stored in their company’s cloud applications.

