Data loss prevention tools are an important piece of your information security tech stack
Data loss prevention is a much bigger topic than just the tools used to help prevent breaches and data loss. IT teams, and all employees, need to understand how to prevent data loss before they put all of their faith in a tool. However, when most people think about data loss prevention, they only think about data loss prevention tools.
There are different types of data loss prevention tools available, many organizations use more than one solution, based on their IT infrastructure. It is important to understand the types of data loss prevention tools available, and the circumstances when you would need to use them.
Why You Need Data Loss Prevention Tools
What is data loss prevention? In simple terms, it is the set of processes, training, and solutions put in place to prevent sensitive information from leaving an organization’s internal data environment.
Organizations face regulations that require them to secure sensitive customer and employee data, these regulations include (but are not limited to) the Fair Credit Reporting Act, the Children’s Online Privacy Protection Act (COPPA), and the Family Educational Rights and Privacy Act (FERPA). Many of these regulations don’t just require proper data loss prevention safeguards, but also periodic compliance audits and breach notifications. The right data loss prevention tool makes all of these requirements possible—and streamlined.
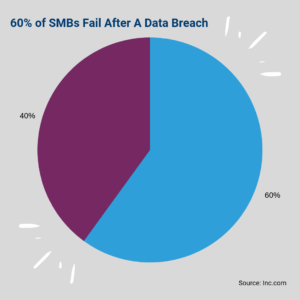
Organizational security is another level where a data loss prevention tool is needed. Information is the true currency of modern business, from the strategic advantage of a company’s intellectual property to the profits criminals make from selling student information on the dark web; information is big money. When a data breach does occur, it can cost the organization hundreds of thousands to millions of dollars. In fact, a recent National Cyber Security Alliance report found that 60% of small and mid-sized businesses don’t survive more than 6 months after a cyber attack.
Closely related to the issue of organizational security is customer trust. When a company or other type of organization experiences a data breach, the people it serves lose trust, this means a loss of customers or student enrollment. A data breach can also impact your customers’ financial security by exposing them to identity theft.
For these three basic reasons, organizations of all types and sizes use data loss prevention tools to run compliance audits and reporting as well as protect sensitive business and customer information.
A Brief Overview of Data Loss Prevention Tools
There are a few different categories of data loss prevention tools available. Some companies provide a full solution suite, while others may specialize in just one or a few areas. Some organizations may need data loss prevention tools for all of the above stated situations, while others may only need one or two tools. It’s important to know what types of data loss prevention tools you need, and how they work with your IT and security infrastructure.
Hardware Data Loss Prevention Tools
There are two ways to secure hardware from data loss: data access security and data recovery.
Data access security includes features such as password keys or the more Sci Fi-esque facial recognition unlock. These hardware data loss prevention tools focus on preventing unauthorized access to the hardware, like an iPhone, and the data stored on it.
The data recovery side of hardware data loss prevention focuses on the ability to reclaim data that has been lost due to hardware (or software) malfunction. So, if you’ve fried the motherboard or the device died, you’ll want to be able to get your important files and family photos back. Most organizations have solved this issue with automatic cloud backups.
A note on data recovery should include at least a brief conversation on recently popularized ransomware. Perhaps the most well known example of this is the WannaCry attack in 2017. But this happens often on a much smaller scale as well. When ransomware first made its debut, many organizations were forced to pay the ransom for their data. They simply could not operate without it.
Today, InfoSec teams use sophisticated data backups to protect against ransomware and hardware failure as part of their broader data loss prevention tool stack.
Endpoints & Network Traffic Data Loss Prevention Tools
An endpoint is any device that communicates back and forth with a network. An endpoint can be a desktop, laptop, smartphone, tablet, or server. Endpoints are targeted because they provide hackers access to an organization’s network and data.
Endpoint security is part of network security, and has become particularly important (and more challenging) with the increase in mobile devices. Employees expect to be able to access work information from anywhere they have internet access. This raises significant data security concerns, as each endpoint is a possible entry point to the network for cybercriminals.
Network security technology incorporates tools such as firewalls, proxies, agents, and/or gateways as a “man in the middle” to filter traffic and access to the network. This is the traditional perimeter security that most people think of when they think of cybersecurity.
Cloud Data Loss Prevention Tools

Pretty much everyone has moved to the cloud for daily business in some way shape or form. Perhaps you are just using email or messaging apps, such as Slack, or you’re using SharePoint for collaboration. Or you’ve gone all in with Google G Suite or Microsoft Office 365. A lot of work is being done in the cloud today, and a lot of data is being stored there.
Until recently, people generally assumed that their network-based cybersecurity tools, such as firewalls and secure gateways, were good enough for cloud security. But data being shared and stored in the cloud acts differently than when it’s managed on-premise, and that has opened unique vulnerabilities for hackers to take advantage of.
[RECORDED DEMO] See Cloud Data Loss Prevention In Action. Click Here To View >>
“The problem with the cloud is that it simply expands the systemic vulnerabilities that have existed since the Internet was developed. The internet was built for redundancy, not security.”
— Will Donaldson, CEO of digital security firm nomx, FOX Business
Data Loss Prevention Tools for Cloud Applications
As organizations move to the cloud, data loss prevention and security are increasingly becoming issues. A combination of open access and lax security infrastructure has led to devastating data breaches.
What Makes Cloud Data Loss Prevention Different?
As previously mentioned, cloud computing results in unique security vulnerabilities. An analogy we like to use is a bar.
When you get there, there’s a bouncer at the door checking IDs. The bouncer is like an agent or a proxy—he’s checking everyone’s credentials and filtering out those who should not have access to the bar. He’s also checking to make sure that there isn’t too much traffic going into the bar so it doesn’t go over maximum capacity.
But what the bouncer at the door isn’t able to catch is what is going on inside the bar. Say some kids with fake IDs get past the bouncer and are getting rowdy. Some of them are starting a fight, one is doing drugs in the bathroom, and another is puking in the corner of the bar. The bartenders (in this analogy, your system admins) are busy at the bar four rows deep and have no idea what’s going on. Sound like maybe it’s time to hire security? We do not condone underage drinking but we do believe this is a good analogy for the benefits of cloud secuirty.
Cloud security tools check traffic coming into and out of your cloud environment (like G Suite and Office 365). They also monitor what’s going on inside of the cloud enviroment. So, those underage kids that are causing a ruckus? The security guards can quickly identify there’s an issue and take action to protect the rest of the people in the bar.
Cloud Data Loss Prevention Features
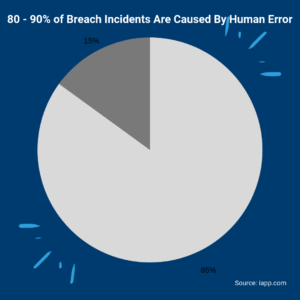
There’s a lot that goes into data loss prevention. First, you need to protect your environment from simple human error, accidental data loss represents 80 – 90% of all data breach incidents. You will also need to protect against malicious internal breaches, which can come from a disgruntled employee. You will then have to protect against external threats. This means quarantining malware and phishing attacks, both in your email platform and file sharing application (like Google Drive and Shared Drives), and removing unauthorized file and/or folder access.
Cloud data loss prevention tools must provide system administrators with easy control over activity in their cloud environment. This means they should be able to quarantine risky emails, files, and folders. They should be able to disable an account that is exhibiting abnormal behavior, and they should be able to discover and remove unsanctioned SaaS applications with risky access permissions. The tool should also allow admins to set up data loss prevention policies, which automate these remediation activities for them thus freeing up their time to focus on other priorities.
Must-have data loss prevention tool features:
- Customizable and out-of-the-box data loss prevention policies
- Ability to control or disable downloading the printing, and copying of files from file sharing, such as Google Drive, Shared Drives, OneDrive, and SharePoint
- Automated and customizable blacklisting/whitelisting of logins by location
- Domain whitelisting
- Suspicious and high-risk behavior alerts
- Unsanctioned SaaS app discovery and risk analysis
- Malware and phishing prevention for cloud-based emails and file sharing applications
- Automatic audits and reporting
API vs Proxy Cloud Data Loss Prevention Tools
There are two completely different types of cloud application data loss prevention software. The difference is rarely talked about, but it is very important. It is the difference between API-based cloud security and proxy-based cloud access brokers.
The main difference in API vs proxy solutions is that a proxy cloud access broker (also known as a cloud access security broker, or CASB) uses traditional network security technology to try to solve cloud security challenges. But as we’ve already explored in this article, network security only secures the perimeter—what’s going in and coming out. These tools don’t adequately secure the activity that is going on once someone gains access (or already has access) to the cloud environment.
This difference is critical to your cloud security. Chances are that you already have network security in place that does the same thing as a proxy-based CASB. If you do, you’re basically duplicating the effort without solving the problem. Further, Microsoft and Google have both published articles advising against using a proxy or agent-based tool to secure their cloud suites.
API cloud security solutions use the application’s native APIs to basically become a native part of the app. This means that API-based cloud security data loss prevention tools are far better at monitoring activity within the application itself. The technology is also able to constantly update with the application itself, so that updates to the application don’t break your cloud security.