Should You Worry About A Google Cloud Security Breach?
As more organizations move to Google G Suite for productivity and collaboration, concerns about the likelihood of a Google cloud security breach are increasing. There is also a lot of confusion about the role and responsibility that Google plays in cloud security for customers.
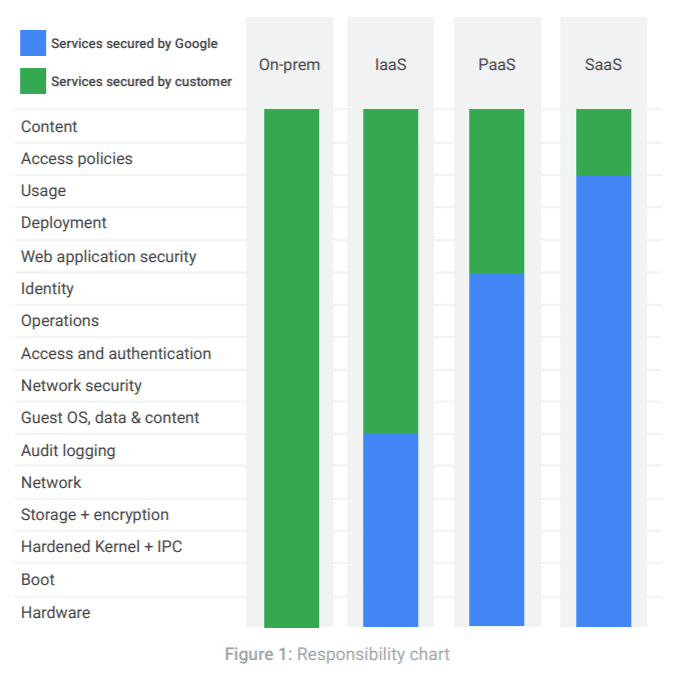
The most important thing for system admins and IT leaders to understand is that Google is only responsible for securing the underlying cloud infrastructure and services that it provides. You are responsible for securing your applications, devices, and systems. You are also responsible for ensuring that you have properly configured your Google cloud security and access settings. This second part, in particular, is where things can go wrong for many organizations using G Suite products.
How Does A Google Cloud Security Breach Happen?
Everyone is familiar with the tried-and-true email phishing attack. These types of attacks are still shockingly effective, despite huge investments in anti-phishing and malware threat protection.
Email isn’t the only way a cloud security breach can occur. As the value of data continues to increase, criminals are finding new ways to gain access to organizations’ data. We’re used to hearing about data breaches affecting millions of records from the likes of Facebook, Yahoo, The Marriott and others. But the best kept secret in cybersecurity is that smaller businesses, K-12 school districts, higher education institutions, and public agencies are increasingly falling victim to cloud security breaches.
Here is a list of how a Google cloud security breach can happen in your cloud environment.
1. Employees
Statistically speaking, employees are the biggest cause of a data breach. Most often it is by accident, but employee actions can also be malicious. Depending on the employee and the permissions granted to them in G Suite, it can be difficult or impossible for Google to identify if an employee is handling your data improperly.
2. Gmail
As previously mentioned, email is still the most common threat vector for phishing and malware attacks. Gmail has made significant improvements in its suspicious content notifications and native email filtering to help users. But many find that it is not enough, thus the huge (and competitive) anti-phishing industry.
3. Google Drive and Shared Drives
Did you know that infected file sharing is another way that hackers can gain entry into your cloud environment? Hackers have figured out vulnerabilities in Google’s security scanning. Hackers can effectively use Google Doc files and Google’s own links against itself to share documents containing malicious links. When this technique is used it circumnavigates Google’s robust Gmail security. One of the ways this is done is by emailing users a link to a Google Doc, which contains malicious links itself. Gmail’s threat protection scanner will only see a Google Doc link, which it will usually assume is safe.
4. Malicious Applications
Another way that hackers will gain access to the data you’re storing in Google cloud is through malicious applications. They may look like games or productivity apps. They can even sometimes resemble legitimate apps. They get users to download the app and login using OAuth credentials, then gain a wide range of permissions to read, write, etc in other applications.
Suddenly, someone has complete access to that user’s Gmail, Google Drive, and more. They might use that access to impersonate the user and get more information about other users, download files with sensitive information, and/or install spyware into the device.
5. Account Takeovers
All of the above Google cloud security breach scenarios can lead to an account takeover. But there are many other ways that an account takeover can occur.
No matter how it happens, a Google account takeover can be devastating for your business or organization and result in long-term financial impacts. Being able to monitor user behavior for a potential account takeover is critical in cloud computing. Google provides admins with great step-by-step instructions on how to identify and secure compromised accounts using the Google Admin Panel.
How Does Google Handle A Cloud Security Breach?
Google takes great care to secure customer accounts and the data stored within them. It’s important for system admins and IT security leaders to understand that Google’s only cloud security responsibility is to secure their cloud infrastructure and services. Customers (that means you) are still responsible for securing their applications, devices, and systems from cloud security breaches.
As a Google customer, Google Cloud provides you with security features such as identity and access management, data encryption, multi-factor authentication, audit logging, and more. It is your responsibility to make sure your security and compliance settings are properly configured.
Google Cloud Security Breach Incident Response
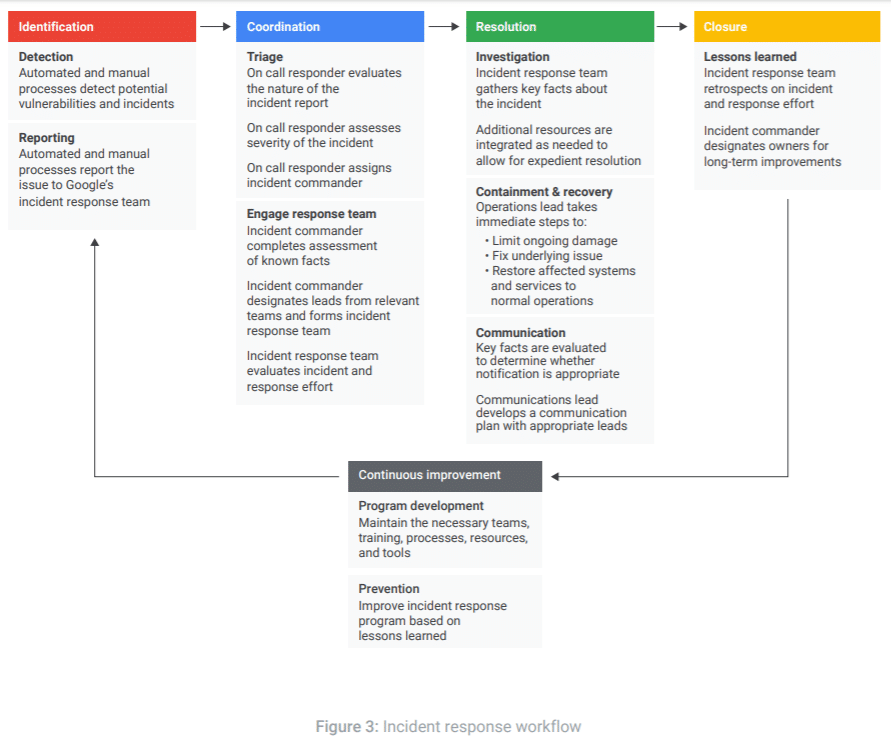
When a cloud security breach happens, Google has a well-documented data incident response process to protect customers’ data. Every incident is unique and must be managed based on the unique needs of the situation. When an infrastructure breach does occur, Google will assemble a response team that may include:
- Cloud incident management
- Product engineering
- Site reliability engineering
- Cloud security and privacy
- Digital forensics
- Global investigations
- Signals detection
- Security, privacy, and product counsel
- Trust and safety
- Counter abuse technology
- Customer support
Again, it’s important to understand that this process is in place to respond to data incidents impacting the Google Cloud infrastructure and services. Google does not roll out the incident response team every time a customer account experiences a data breach or incident. That is your responsibility!
The Admin console is a great place to manage your security and compliance settings and more. Some organizations also find it sufficient to identify and remediate a data breach in their Google cloud environment. But, if you’re like most people responsible for the data security of your cloud environment, you may want to consider an additional cloud application security platform.

