OAuth is a very good security standard that has been carefully designed to balance user experience and security and is a solid security protocol that has been used across many apps. OAuth is a standard many SaaS vendors support for REST API access. When something is as popular as OAuth, it quickly becomes an attractive target for hackers and bad guys, like with yesterday’s Google Docs attack.
There are indications that Russian-based spies are starting to leverage loopholes in end-user cognition to get access to corporate data. This is a clever mix of social engineering and exploiting user familiarity. The goal is to conduct corporate or political espionage or to use the data to demand ransom from targeted companies. Trend Micro has dubbed this attack “Pawn Storm”.
This Gmail attack works by asking the user to grant permissions to specific capabilities in Google G Suite, including the ability to read and write emails and documents, and access user information such as name, email address, age etc. Below are some potential scenarios:
- An email sent from what appears to be the CEO to CFO authorizing payment to a third party
- CryptoLocker-style attacks
- Analyze sharing behavior and identify with which other domains the company has been sharing documents
- A targeted corporate espionage program intending to predict upcoming M&A or funding activities
The sky is the limit for a skillful hacker once they get access to a targeted individual corporate Gmail and G Suite account. A more sophisticated attacker might even plant their code and strike at the perfect moment for maximum impact. In the case of yesterday’s Google Docs attack, it appears to have been carried out by an inexperienced hacker who went for maximum publicity instead of maximum damage. (Likely script kiddies, but we won’t ever know for sure.) Fortunately, Google reacted quickly and shut them down. However, not every attack will be as visible as that one.
You can read about the Google Docs attack in yesterday’s article on NetworkWorld.
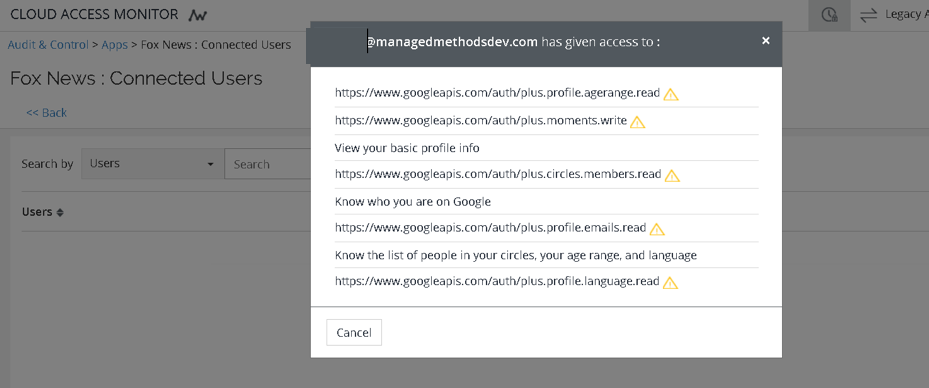
Even some seemingly benign apps ask for broad permissions. For example, the Fox News app requests permission to read your email. That means that if the Fox News app is compromised, your organizational data may also be compromised. It’s never a good idea for employees to use corporate Gmail for these type of consumer applications, but they often do it anyway for convenience.
How to Protect Your Company Against Attack
Most advice on how to defend against this type of attack is focused on users checking the permissions they granted to different apps. However, this advice falls short for enterprises since it is harder to enforce due to limited visibility.
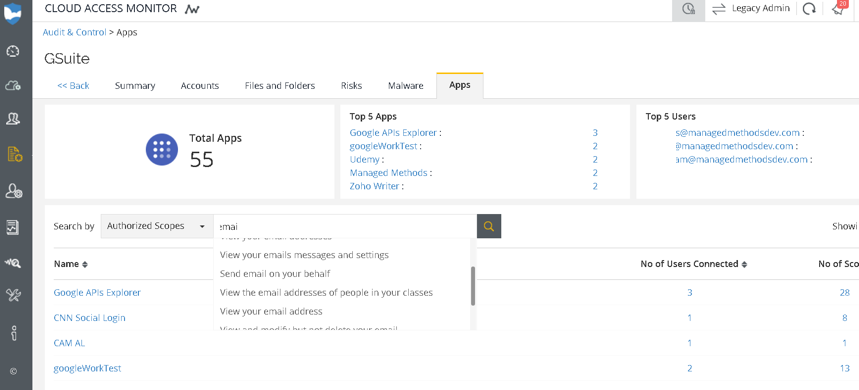
ManagedMethods’ Cloud Access Monitor tool provides that critical visibility, so an administrator can review all the apps that employees have authorized and what permissions were granted to those apps:
Administrators can also search which apps have permission to read users’ emails or access documents in G Suite:
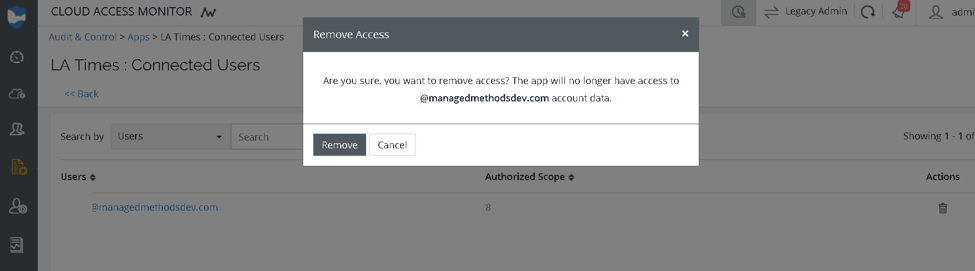
And finally, administrators can revoke access to these apps right from Cloud Access Monitor:
Don’t wait for another phishing attack to put your company at risk. Request your free Third Party App Permissions Audit today.