Free Cybersecurity & Student Safety for Google Workspace and/or Microsoft 365
Google workspace and Microsoft 365 security & safety monitoring made easy for K-12 it teams—no proxy, no agent, no extension, and no special training needed
***You must have admin-level access to your district’s Google and/or Microsoft 365 domain to activate a free trial***
ManagedMethods is the leading Google Workspace and Microsoft 365 cybersecurity, student safety, and compliance platform for K-12 school districts.
ManagedMethods uses cloud-native API integrations to help district IT admins secure sensitive data and monitor for student safety signals on any device, from any location. The platform uses artificial intelligence-powered malware and phishing threat protection, detects and remediates account takeovers, and secures data from malicious and accidental breaches. Out-of-the-box and customizable data loss prevention policies allow IT admins to automate enforcement, including notifications, password resets, unshares, and other tasks without the need for custom coding or switching to different tools.
Turnkey and customizable policies detect signals such as cyberbullying, self-harm, discrimination, threats of violence, explicit content, and domestic abuse in both text and image content. ManagedMethods does not collect or store any student information, nor do company employees view any information without the explicit request of district administrators in the context of a product support ticket.
WHAT TO EXPECT WHEN YOU SIGN UP FOR A FREE TRIAL
STEP 1: One of our area reps will reach out to you with a few confirmation questions & schedule a “kick-off” call to walk through the product with you
STEP 2: You will receive an activation email with step-by-step instructions. You must have admin-level access to your district’s Google and/or Microsoft 365 domain to activate a free trial
STEP 3: Your area rep and a member of our customer success team will meet with you during your scheduled “kick-off” call to walk you through the product and answer any questions you may have
STEP 4: 30 days of full, unencumbered product access to see what security and safety risks you’ve been missing! During this time, don’t hesitate to reach out to your support staff here at ManagedMethods. We’re here to help!
Get Your Free Trial Today
Our customers




































































Testimonials
What our customers are saying
“Give ManagedMethods a try! I recommend it to other districts that are looking for this type of solution. The free trial is full-blown, so you’re truly able to demo the full product before you buy. And it’s absolutely worth it to help keep our kids safe.”
Wes Rhodes
Network Administrator - Lenoir City Schools, TN
“ManagedMethods is easy to use and easy to do business with. This alone brings down the Total Cost of Ownership—the fact that it is affordable for school districts made our purchase decision easier. We thought it was a great product from the start and as we’ve used it over the years, we continue to see value in our decision.”
Vince Humes
Director, Innovative Technology Solutions - Northwest Tri-county LU5, PA
“I appreciated that ManagedMethods offers a 30-day free trial. It’s great to be able to run a test in your own environment and make sure it’s going to do what you want it to do—and what sales and marketing say it’s going to do. It’s also a huge benefit to find the risks that you don’t know are there.”
Vaughn De Fouw
Infrastructure Engineer - Kettle Moraine School District, WI
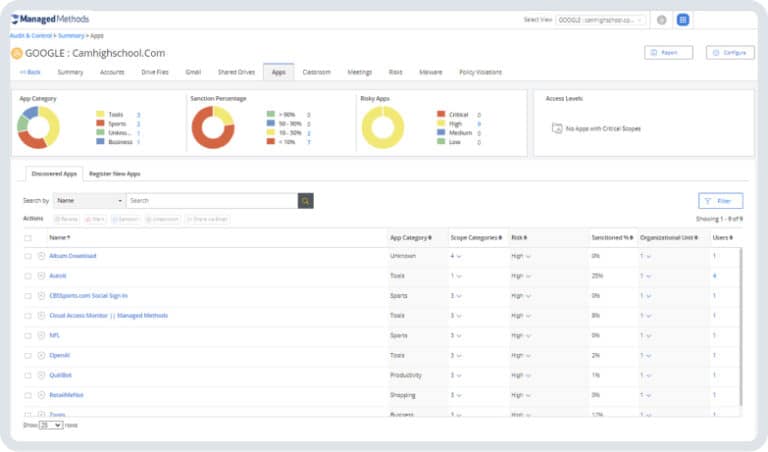
Control 3rd party apps
Cloud Monitor automatically scans OAuth permissions granted to 3rd party apps 24/7, assigns a risk score, and allows admins to set up automatic remediation based on customizable rules. 3rd party app risk scores in Cloud Monitor are based on:
- The scope of required admin privileges.
- The presence of write permissions.
- The status of authorization within your specific environment.
- The endorsement status in other Cloud Monitor user environments.
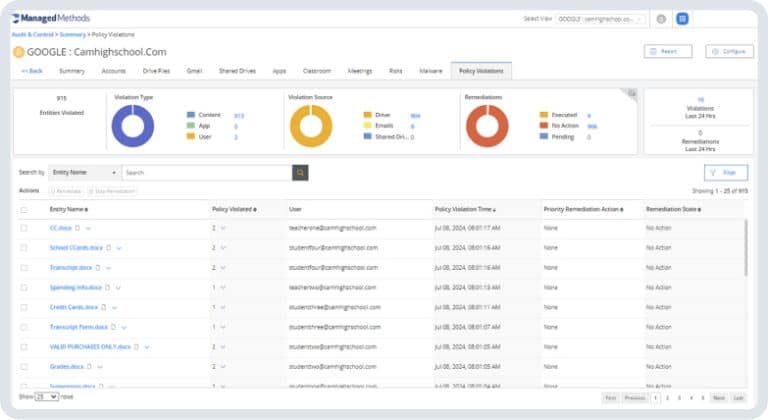
Data loss prevention
Student and staff data in school systems are prime targets for cyberattacks, often due to accidental exposure. District IT teams need to manage access to this sensitive information in Google Workspace and Microsoft 365 to comply with regulations and safeguard both students and staff.
- Detect anomalous events that indicate unauthorized access to data.
- Identify when data is being improperly emailed or shared.
- Automate data loss prevention to protect social security numbers, W2s, payment, health information, and more.
- Continuously monitor behavior in Google Workspace and Microsoft 365 and automatically mitigate data security risks.

Phishing & malware threat protection
Phishing remains the leading method for criminals to access school accounts, with a marked increase in malware and ransomware attacks. If your district is using Google Workspace and/or Microsoft 365, criminals can access sensitive student and staff information via email, file sharing, and risky third-party apps.
- Scan internal & external emails for phishing and malware threats in the message body, attachments, and links.
- Automatically quarantine or delete emails and shared files containing phishing and malware links.
- Identify risky 3rd party applications connected to district Google and Microsoft accounts through OAuth.