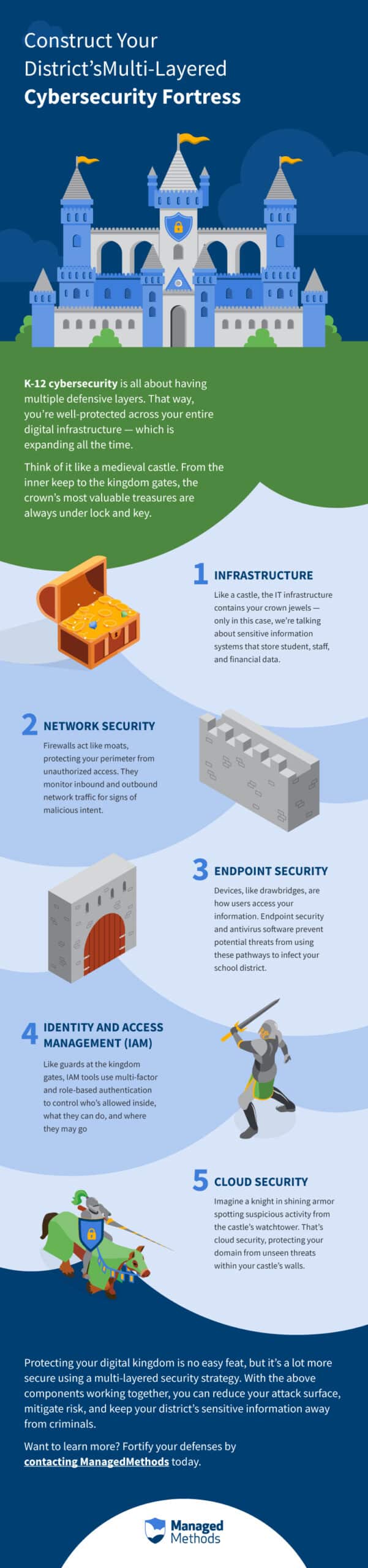
K-12 Cybersecurity is all about having multiple defensive layers
Think of your district’s digital infrastructure as a medieval castle.
It houses your most valuable treasures — academic records, student data, and sensitive information.
Outside the castle walls, your network security forms a moat to protect the crown jewels from unauthorized access and attack. The only way to enter is by crossing a drawbridge, where guards check all traffic for signs of a potential threat.
Although it seems simple, this approach is a tried-and-true method for mitigating cyber threats of all shapes and sizes. Why? Because it uses multiple security measures to continuously monitor and stop hackers before they reach the inner keep.
Additional cybersecurity and student safety resources:
Category
Infographics
Share