ManagedMethods helps K-12 IT admins audit and investigate Google Meet access
As we get into the swing of things in the new school year, districts are continuing to work through a variety of challenges that COVID-19 has created. Along with the continuing issues of student access, attendance, and engagement, districts are again dealing with “Zoom-bombing” incidents. That is, when Zoom is actually up and running…
Many districts are turning to G Suite for Education to enable remote learning. While Zoom is getting most of the heat for disruptive attacks, Google Meet is by no means immune to “bombing”.
Google responded to Google Meet “bombing” incidents by rolling out an update that does not allow anonymous users to join a Meet organized by anyone with a G Suite for Education or G Suite Enterprise for Education license. This protection is now turned on by default and reportedly rolled out to all education domains in late July.
However, we’re now hearing about a small number of Google Meet “bombing” from our customers, as well as our own team members who have school-aged children. So, we wanted to highlight how ManagedMethods’ new Google Meet Analyzer can help IT admins audit their districts’ Google Meet behavior.
Auditing Google Meet “Bombing” & Other Behavior
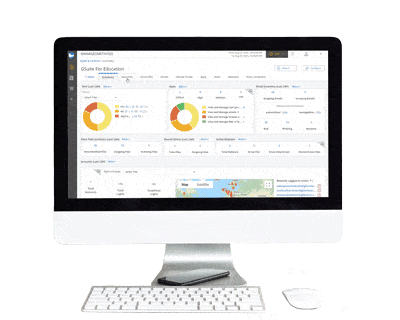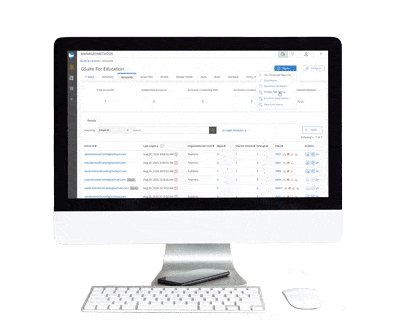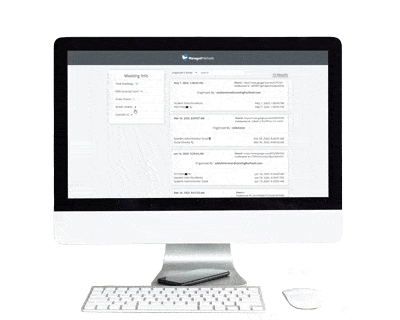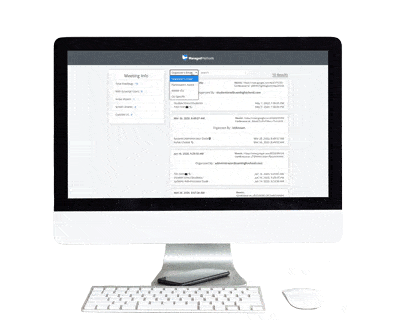
Using our Google Meet Analyzer, IT admins can quickly and easily see Meet participants and organizers by individual user and organizational unit (OU). You can see Meets that included a screen share, and ones in which external domains accessed the Meet.
Admins can further drill down to see which IP and email address a Meet participant logged in from. This information helps determine if the behavior was likely caused by a student misbehaving or an unauthorized user that somehow gained access to an internal user account. This information helps your teachers and/or administrative staff determine if corrective actions need to be taken with the student.
It can also help you determine if there is a problem with unauthorized account access, which would require investigation into account takeover and data security actions. In this case, ManagedMethods provides easy tools to investigate and take remedial action on the account for cybersecurity purposes.

