Whichever you choose, a zero-trust security model is critical for effective hybrid learning security
The challenges presented by the COVID-19 pandemic just keep on pouring in. Most districts are now concerned about how to provide devices for hybrid learning. According to our recent poll, over 60% of districts are planning for some level of hybrid learning in the coming school year. IT leaders in these districts are facing many issues, and whether to roll out a 1:1 vs. BYOD program is high on their lists.
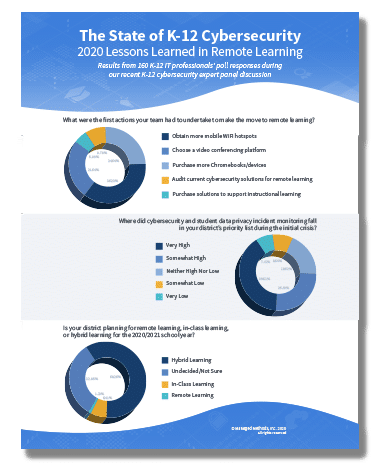
Most of the information you’ll find about the pros and cons of 1:1 vs. BYOD focuses on considerations such as cost, maintenance, management, and equitable access. Few discuss the data security needs that need to be addressed. If your team is working on either making a 1:1 vs. BYOD decision, or you’ve already made the decision and you’re in the midst of rolling your program out, hybrid learning security considerations need to be flushed out for both 1:1 and BYOD scenarios.
What is Hybrid Learning Security?
Securing school networks and data is a critical issue for all districts at all times. But in the upcoming hybrid learning environment that will be new to many school districts, data security will be a bit different than what most K-12 IT leaders and security admins are used to.
The shift to K-12 remote learning in the spring of 2020 led to plenty of cybersecurity challenges. For example, one of the hottest cybersecurity topics for district IT teams this summer is how to control 3rd party apps that were connected to their domains in the spring (and going forward). Now that hybrid learning is here, you’ll have students in the classroom at some times, and learning remotely at others. This hybrid learning model is going to present new security challenges.
The hybrid security environment is unique because students and teachers won’t just use the school building’s network. They’ll also use their home network. Any malware, spyware, etc. they pick up when their devices are not protected by the school’s network security could end up on your network when they return to the classroom.
The zero-trust security model has been popular among both small and large businesses for years, and it’s time for school districts to start implementing this type of cybersecurity infrastructure. It focuses on securing access to data, rather than only controlling access to networks. It also allows you to secure sensitive information no matter what device is being used or where users are when they access school cloud apps. It also provides an additional protective layer around sensitive data, should an attack breach your network.
“I’m not overly concerned about students and teachers using public or unmanaged networks for the simple fact that I treat all endpoints as hostile to begin with. Whether I own them or not, there is zero trust there.”
Neal Richardson,
Director of Technology @ Hillsboro-Deering School District
Quote from The State of K-12 Cybersecurity & Student Data Privacy Panel Discussion
![[FREE WEBINAR] Google Classroom and Beyond: Attendance, Safety, and Security in Hybrid Learning Environments. REGISTER >>](https://no-cache.hubspot.com/cta/default/6834707/ef0f9567-54ab-49fa-9dc1-ab1ad88f05cb.png)
Comparing 1:1 vs. BYOD in Hybrid Learning Security
The question for many district IT teams is: Which device model is best? From a hybrid learning security standpoint, there are pros and cons to both.
Securing 1:1 Devices
Though the upfront cost of a 1:1 program is higher than BYOD, it does make K-12 hybrid learning security quite a bit easier. District IT admins have more control over 1:1 devices in areas such as the types of security software used and device-level security settings and configurations.
They also have access to a greater number of device and extension-based content filters and student safety monitoring solutions that are available on the market to meet CIPA compliance requirements. There is also greater availability of device-based antivirus and remote access software that makes it easier to protect the devices and assist users if there’s a problem.
IT admins will still need to monitor and control access to accounts and files stored in their cloud applications, even with a 1:1 program. This is because device and extension-level security tools don’t have the capability to monitor activity happening within cloud applications, such as G Suite and Microsoft 365.
Keep in mind, too, that even if you decide on a 1:1 device plan, you’ll probably have some teachers, staff, and students who use their own device from time to time. For example, if a student forgets to bring their school-provided device home, they’ll undoubtedly end up using their own device for accessing remote classrooms and doing their homework. Therefore, your 1:1 hybrid learning security plan needs to be able to secure access to school cloud apps and information regardless of the device being used.
Securing BYOD Devices
BYOD programs seem more cost-effective for school districts because they can avoid upfront costs for acquiring the right number of devices. But a BYOD program comes with a long list of process, management, support and accessibility issues that may reduce the program’s cost-effectiveness over the long term.
For many districts, the Spring 2020 remote learning experience created a de facto BYOD program. Students and teachers, in many cases, needed to use their home computers to log in for remote learning. This is causing huge security problems for districts that don’t have cloud monitoring capabilities in place.
Districts opting for a BYOD program will be more reliant on cloud-based content filtering, access monitoring, and data security tools to keep their student, staff, and business data secure because they won’t have as much control over students’ personal devices. Cloud-based security also helps keep students safe and districts compliant with FERPA, HIPAA, CIPA and other regulations.
Cloud Security for 1:1 and BYOD Hybrid Learning
Regardless of which device model your district decides to use for hybrid learning, cloud application security is a critical element of building a zero-trust security posture. If your district is using G Suite and/or Microsoft 365 for the coming school year, that means your district is going to be storing a large amount of sensitive data in the cloud.
That means you need to incorporate cloud security tools into your cybersecurity infrastructure. It provides broad benefits for both 1:1 and BYOD initiatives for districts that are planning for hybrid learning in the fall. Cloud-based monitoring and management give IT admins the ability to maintain full visibility and control over data access and user behavior—whether students are logging in from home or the classroom. It also helps to keep your network free of cybercriminals or other “bad guys” when devices used at home reconnect to your network.
If your district is evaluating your own 1:1 vs. BYOD decision, you need to consider the unique security issues that hybrid learning presents.

