No, Cloud Monitor is not a content filter. The platform does not block access to websites, domains, and other types of content. However, we are happy to announce the availability of our new, innovative Content Filter product, which you can learn more about here.
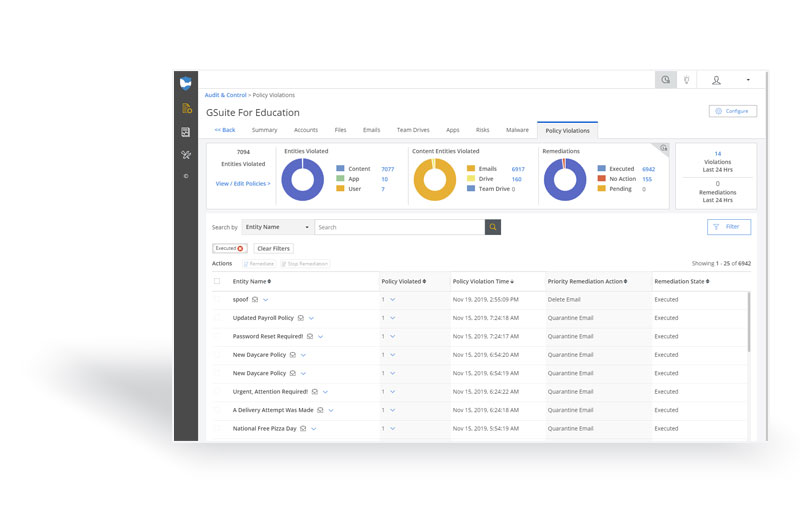
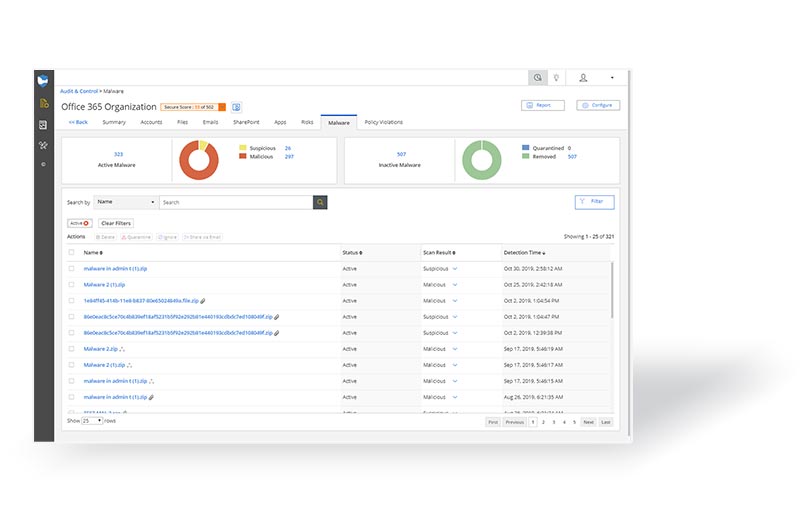
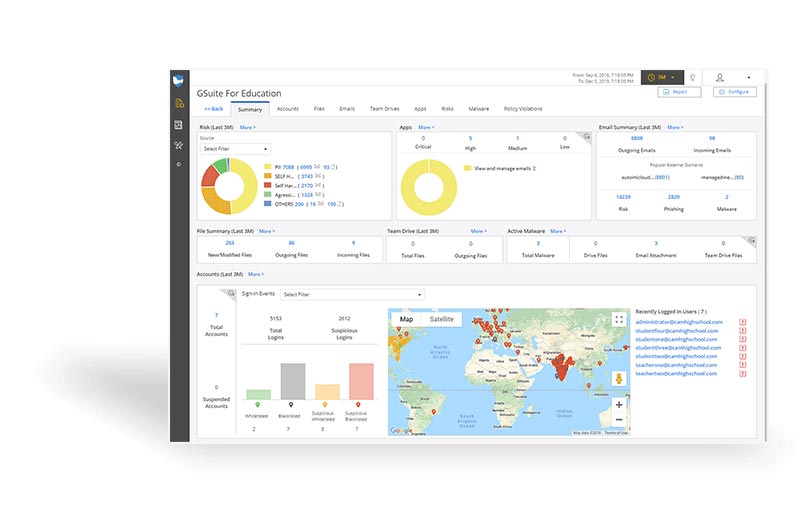
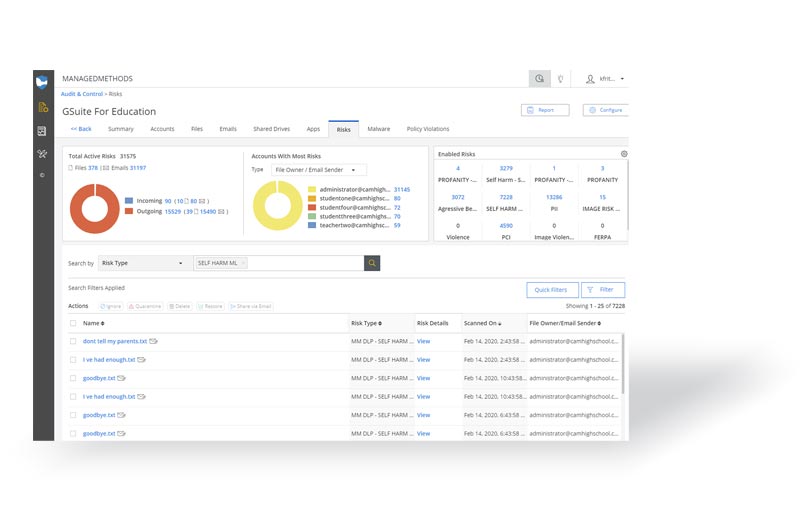
Cloud Monitor scans your district’s Google Workspace and/or Microsoft 365 domain to detect content based on specific parameters (we call “risks”) that are set up using contextual keywords, regex text, and numerical strings, and artificial intelligence. Cloud Monitor is capable of scanning for different types of content within your domain for both data security and student safety use cases.
For example, it can detect when a file containing personally identifiable information is being shared outside your domain and/or globally and automatically break the share. The platform can also detect when explicit images are being uploaded and/or shared from your district’s shared drives, email, and chat apps.
Cloud Monitor specifically works to detect risks inside Google Workspace for Education apps currently including Gmail, Drive, Shared Drive, Docs, Slides, Sheets, Chat, Meet, and Classroom. In Microsoft 365, the platform works to detect risks inside Microsoft’s cloud-specific environment (not on-prem software), including Outlook, Word, PowerPoint, Excel, SharePoint, and OneDrive.
To learn more about the K-12 cyber safety and security layers, and how Cloud Monitor fits within them, read more here.