The Role of Technology in Cybersecurity & Safety
Cloud Security Solutions for Public Institutions | TX DIR Forum 2019 from ManagedMethods
Earlier this week, I traveled to Austin, Texas to join the Texas Department of Information Resources (DIR) Information Security Forum. I was invited to lead a session on how cloud security can help public institutions secure sensitive data stored in the cloud and help safety management teams keep employees, students, and others safe. It was a fantastic discussion, and very well-received by attendees. Here is a brief overview of what we discussed.
1. Information Security Needs To Take A Layered Security Architecture Approach
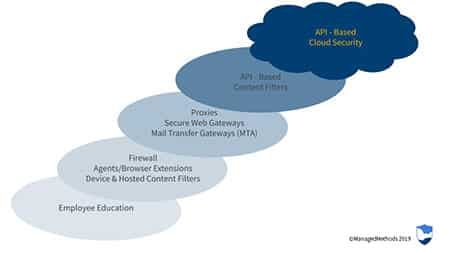
There is no cybersecurity “silver bullet” (cliché, I know, but true). Information security pros layer security to provide both comprehensive and redundant protection. In many areas of business, redundancies are a bad thing. But in cybersecurity and campus safety, where the consequences for failure are high, redundancy is necessary. During the session, we talked about the different layers of cybersecurity that attendees use today, and answered questions about some that they were less familiar with.
- Employee Education: I think every IT security pro out there knows that the single greatest point of failure in cybersecurity is the people using the information. Human error causes far more data breaches than malware or any other type of malicious attack. In fact, a recent report found that 1 in 4 workers are aware of security guidelines, but choose to ignore them! This is why ongoing employee education is the foundation for any good security strategy.
- Network Security: Sometimes referred to as perimeter security, this layer includes your firewall, agents, browser extensions and the like that protect the perimeter of your network environment. This layer represents the more traditional, common approach to cybersecurity that should be part of your infrastructure to protect on-premise servers, software, and your network.
- Web Security: Web security takes things to the next step by placing technology similar to a firewall in front of off-premise information, such as the cloud. These tools include cloud access security brokers (CASB), proxies, secure web gateways, and mail transfer gateways (MTA). Web security can also be referred to as “man-in-the-middle” security features that most commonly focus on securing access to cloud environments.
- API – Based Content Filters: To be clear, not all content filters use APIs. Some types of APIs would land in the last layer. API content filters work differently than proxy based filters in that there is no “man-in-the-middle”, they integrate directly with the cloud application in use.
- API-Based Cloud Security: If your organization uses cloud applications for operations, such as Google G Suite or Microsoft Office 365, API-based cloud security is a requirement. This is because none of the other layers can protect or monitor the information stored and shared in the cloud. They can only monitor access going into and coming out of it. Cloud security tools provide IT security with the visibility and control they need to secure sensitive data and remain compliant with regulations.
2. Why Cloud Security?
Next, we took a deeper dive into cloud security. Many people don’t realize just how important cloud security is. Many think that if they have a firewall and a gateway, they’re covered. This simply is not true. With cloud computing there is no perimeter. If there is no perimeter, there is nothing for the firewall to protect. Traffic can easily bypass firewalls and gateways to gain access to cloud environments.
There are also legal reasons and compliances that require organizations to use cloud security. If you are storing student, employee, and/or customer personally identifiable information in Google Drive or SharePoint, for example, you need to secure it. And, again, a firewall or gateway simply won’t do the trick.
Cloud security solutions provide IT security teams with control over the information and account behavior within cloud applications. They can see who has access to what files, what is being shared with whom, and much more. IT teams get threat protection, data security, and user behavior & monitoring with a good cloud security tool.
FREE CONTENT FILTER COMPARISON GUIDE FOR K12 SCHOOL DISTRICTS >>
3. What Does Safety Have To Do With Cybersecurity?
Cybersecurity and safety are closely related in several ways. Cyberbullying in schools and in the workplace have led to devastating incidents on-campus, with workplace violence, suicides, and school shootings becoming a depressing norm in U.S. society. Further, there are incidents of unwanted sexual advances, explicit and/or offensive content being shared throughout the office or school. This type of behavior is more than just a distraction.
Finally, criminals and hackers are finding ways to use smart building technology to gain access to buildings, spy on workers and meetings, and threaten students. These types of incidents are not just people trying to harass or otherwise “get a rise” out of people. In some cases, they’ve attempted to run ransom schemes by threatening violence and more through campus surveillance systems.
4. What Is The Difference Between Cybersafety and Cybersecurity?
Cybersecurity’s role is to protect technology infrastructure and information from unauthorized access and attacks. Cybersafety focuses on protecting the physical and emotional well being of employees, faculty, and students using the technology.
Cybersecurity protects information like social security numbers, names, addresses, HIPPA health information and more that are stored in networks, computers (or other devices), and in the cloud.
Cybersafety scans for explicit content, threats of violence, self harm, and cyberbullying. Technology can be used to filter domains, scan email, documents, images, messaging apps, and even social media channels to flag potentially harmful content and alert the proper authority to handle it before it becomes a bigger issue.
As our lives are more and more entwined with technology and the digital world, cybersecurity and cybersafety will only continue to merge. IT and security professionals need to recognize this and work together to keep people safe and their data secure. ManagedMethods is a cloud security platform that helps education, public sector, nonprofits, and mid-sized companies do just that. Our platform is used to secure over 1,000,000 user accounts (and growing) as well as help IT professionals gain control over how information in all those accounts is being stored, accessed, and shared.
It was a great pleasure to meet and talk with the attendees at the 2019 DIR Security Forum. If you have a chance to go to this FREE event next year, I highly encourage it!

