When it comes to ransomware attacks, the notification that your data has been encrypted is not the beginning. It’s typically the result of days, weeks, or even months worth of effort. Monitoring for ransomware indicators means that you can detect ransomware early warning signs to stop, or at least reduce the impact of, an attack in its earliest stages.
ManagedMethods cloud security and safety platform provide a variety of monitoring and security tools to help reduce the chances of ransomware—and even phishing—attacks in your district’s Google Workspace and/or Microsoft 365 domains.
4 Ways ManagedMethods Helps District Tech Teams Identify Ransomware Indicators And Take Action
Here, we provide an overview of critical monitoring areas and best practices to help you detect ransomware indicators to avoid an attack in your district’s cloud environment. We’ll discuss how to identify indicators of attempted attacks, possible account compromisations, and concerning data oddities using ManagedMethods.

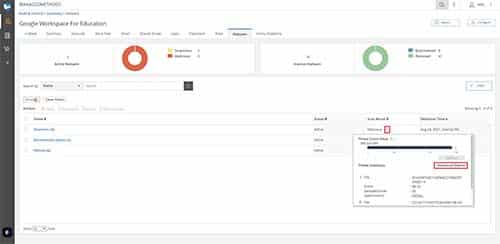
1. The Malware Tab
ManagedMethods partners with BlackBerry Security (formerly named Cylance) to scan for potential malware risks in your district’s Google and/or Microsoft 365 domains. This includes emails as well as drive files and shared drive files.
BlackBerry Security uses AI in combination with signature scanning, to find novel and known malware. This provides true zero-day protection for your cloud environment. BlackBerry Security also looks for malware that uses memory maliciously and allows immediate responses through policy enforcement in the ManagedMethods console.
When malware is found in your environment it will be displayed on the Malware Tab. There are two different scan results for malware:
- Malicious: Malware that is known to be malicious, or a file that is behaving maliciously. Files that are marked malicious should be treated as active malware and dealt with accordingly. It is incredibly uncommon for a file to be marked as malicious that is not.
- Suspicious: Files marked as suspicious are files that seem to be behaving maliciously, however, the AI is unable to verify the file as truly malicious. These files should be examined to see why they are triggering the flag.
In ManagedMethods, you can download a scan report to see why it was marked as malware. You can also find detailed information about the file that was flagged to see information such as who created it and when, who modified it last and when, who it was shared by and with, and more in just a single click.
As you’re investigating a malware risk, some questions to ask yourself include:
- Is the creator/sender internal or external to my domain?
- What type of file is this?
- How many users received this content? (internal vs external)
- Is the end user(s) someone with high-level domain and information access? (ex. student accounts vs staff like superintendents)
Taking Action In ManagedMethods
The goal here is to have zero results for “active malware” in the malware tab. Using ManagedMethods, you can quickly:
- Delete: Permanently delete the file from your cloud environment
- Quarantine: Move the file to a folder in the administrator’s Google/Microsoft drive for further investigation
- Ignore: If the file is not a threat, you can ignore it. This will leave the file in place but remove the threat result from the summary in ManagedMethods
- Share Via Email: Send the information to someone outside the ManagedMethods platform for further investigation
2. The Email Tab
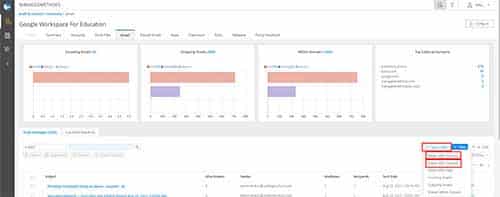
ManagedMethods also partners with BlackBerry Security for malware detection in your cloud-based email apps, Gmail and Outlook. Additionally, the platform uses three methods to scan for potential phishing risks: Google’s Webrisk API, The Phishtank Consortium, and internal phishing content scans.
In the Email Tab, ManagedMethods provides quick filters to identify emails with malware and phishing. Just like in the Malware Tab, with just one click in the results, you can dive into the details of any particular email that is flagged to find out information such as who sent the email, who received it, whose mailboxes it is in, and the message body of the email.
As you’re investigating email malware and phishing risks, some questions to ask yourself include:
- Is the sender internal or external to our domain?
- Does the email contain any attachments?
- How many recipients were part of this event? (internal vs external)
- Is the recipient someone with high-level domain and information access? (ex. student accounts vs staff like superintendents)
Taking Action In ManagedMethods
Using ManagedMethods, you can take both one-off and bulk actions on ransomware indicators you find in your domain.
One-off action options include:
- Download: Download the entire body of the email for further investigation
- Preview: Open a preview of the email in a new tab to see the context without having to download
- Share Via Email: Send the information to someone outside the ManagedMethods platform for further investigation
Bulk action options include:
- Delete: Permanently delete the email from all users’ inboxes
- Quarantine: Move the email to all users’ Trash
- Restore: Move a quarantined email out of users’ Trash
- Share Via Email: Send the information to someone outside the ManagedMethods platform for further investigation

3. Identify & Investigate Anomalous Activity
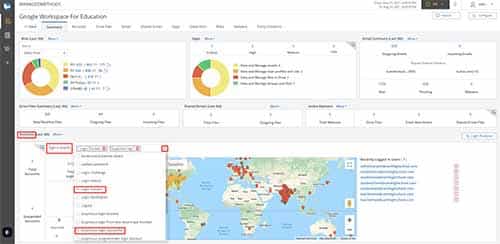
ManagedMethods’ Summary Tab provides admins with an overview of quick data points related to activity in your district’s email, drives, shared drives, logins, risks, and more.
Some common indicators that a ransomware attack is underway, or that your district may be being targeted, that can be surface on the Summary Tab include abnormal login locations, abnormally high login failures, abnormally large number of emails being sent from or to your users, and an abnormally large number of files being shared into your domain. Of course, you can also see an overview of the number of phishing and malware risks in your domain from the Summary Tab. It also provides quick access to each of these areas, and more, to take you where you need to go in the platform to drill down into the details of each risk.
As you’re investigating anomalous activity risks, some questions to ask yourself include:
- Are the logins “Event Type” relating to success access or other attempts resulting in denied access outcomes?
- Are the successful login events related to a concerning Location?
- Are the Location details exposing VPN-related service providers?
- Do the login event times appear to be unordinary access times?
Taking Action In ManagedMethods
Taking action on these risks will largely depend on what type of behavior you’ve found. Examples of some actions you can take to remediate abnormal activity in your domain include:
- Suspend Account: Suspend the user account to prevent logins or other behavior by the user
- Change Password: Allows you to reset and then manually assign a new password for the account
- Unsuspend Account: If an account has already been suspended, you’re also able to unsuspend the account
- Have I Been Pwnd: ManagedMethods connects with this popular database that documents publicly known data breaches. If the user was found in this database it will return the compromised source and the data leaked during the event
4. The Apps Tab
According to a Security Intelligence report, over two-thirds of malware downloads originate from cloud apps. This means that, beyond student data privacy concerns and compliance, controlling the third-party SaaS apps that have access to your district’s data is crucial for cybersecurity and ransomware protection.
Identifying and controlling your district’s third-party apps is one area where the ManagedMethods platform really shines. ManagedMethods clearly shows you what apps are most risky, mainly based on the app’s access and management levels. For example, apps that have access to view, edit, and send emails, files, users, roles, and/or groups and OUs have a very high level of access.
To be sure, there are some apps where these access levels are necessary. But there are also many, many more where it’s not. Vendors whose apps have a high level of access to your district’s data should definitely be properly vetted for data use and security compliance.
The Apps Tab in ManagedMethods will break down the total number of apps that are connected to your domain into four levels of risk: Critical, High, Medium, and Low. You will also get a breakdown of your apps by “Sanction Percentage”, which is based on how many ManagedMethods users across all customers have sanctioned an app. Additionally, the Apps Tab provides a breakdown of all your apps by App Category.
There is so much more you can do to control apps in your district’s Google and/or Microsoft domain. I definitely encourage you to schedule a demo to dive into this tool deeper.

As you’re investigating risky apps, some questions to ask yourself include:
- Is this a known app that needs to be used?
- Has this app been reviewed and received a safe sanction status?
- What users have granted authentication into the app? (ex. students and/or staff)
- Does the application scopes grant concerning and/or unnecessary access powers?
- Based on access levels, would a bad actor be able to generate internal attacks on the behalf of a compromised user account?
Taking Action In ManagedMethods
Using ManagedMethods, you can take both one-off and bulk actions on risky third-party apps you find in your domain.
One-off action options include:
- Remove: One-time removal of users’ access to the app (and the app’s access to your domain’s data)
- Warn: Send a warning to the user to remove the app
Bulk action options include:
- Revoke: One-time removal of users’ access to the app (and the app’s access to your domain’s data)
- Warn: Send a warning to the user to remove the app
- Sanction: Set the app to a sanctioned status, this will affect its risk score
- Unsanction: Remove the sanctioned status from an app, this will affect its risk score
- Share Via Email: Send the information to someone outside the ManagedMethods platform for further investigation
Policies in ManagedMethods: Automating Ransomware Indicator Detection & Remediation
ManagedMethods allows you to create automated alerts and remediation actions based on specific conditions using policies. This is another area where the platform really shines above the rest and makes cloud security and safety easy for time-strapped district tech teams.
Basically, all of the action items discussed above (plus so much more) can be automated through policies in ManagedMethods. This means that, rather than going in and manually taking action, you can get the platform to work for you.
I’ve heard it time and time again from our customers — “ManagedMethods helps me sleep at night.”
This is because they’ve set up policies that automate actions that remediate their biggest concerns, so they can get a restful night’s sleep or even take a relaxing vacation!
If improving your district’s cybersecurity stance is on your project list, now is the perfect time to take a look at ManagedMethods. Schedule a demo today to learn about more of the unmatched visibility and control that your fellow K-12 tech teams are enjoying.